Introduction
This document presents data from the research carried out for the article "Detecting and Mitigating DDoS Attacks with Moving Target Defense approach based on automated flow classification in SDN networks.". The source code of the applications developed for this study can be verified in the GitHub repository . A demonstration video of the operation of the project is presented.
ATTACK BAD TCP FLAGS (ALL FLAGS SET) WITH RANDOM FOREST SENSOR
Graph data: CVS File
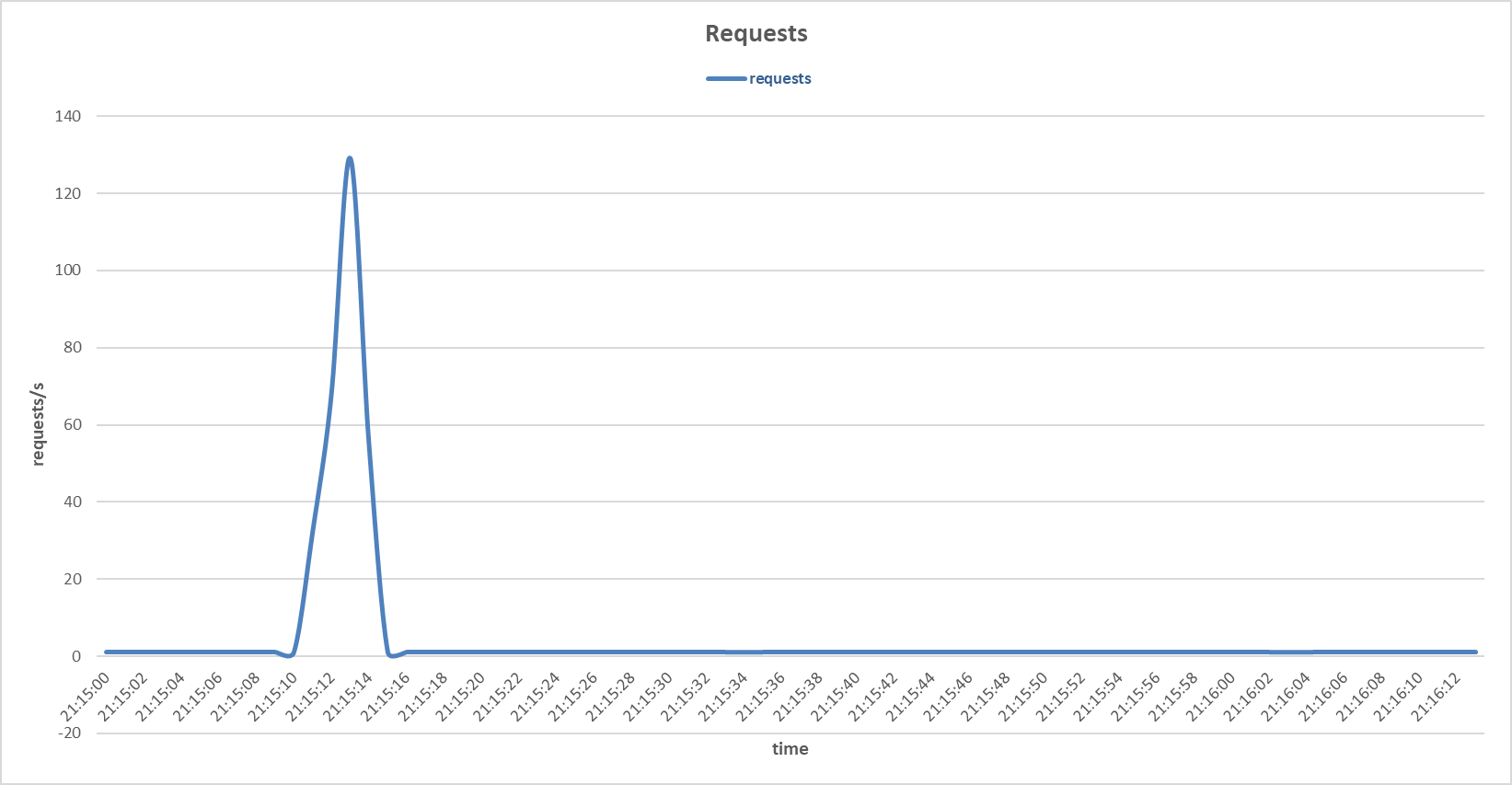
Requests to the primary server during Bad TCP flags (All Flags Set) attack with Random Forest sensor.
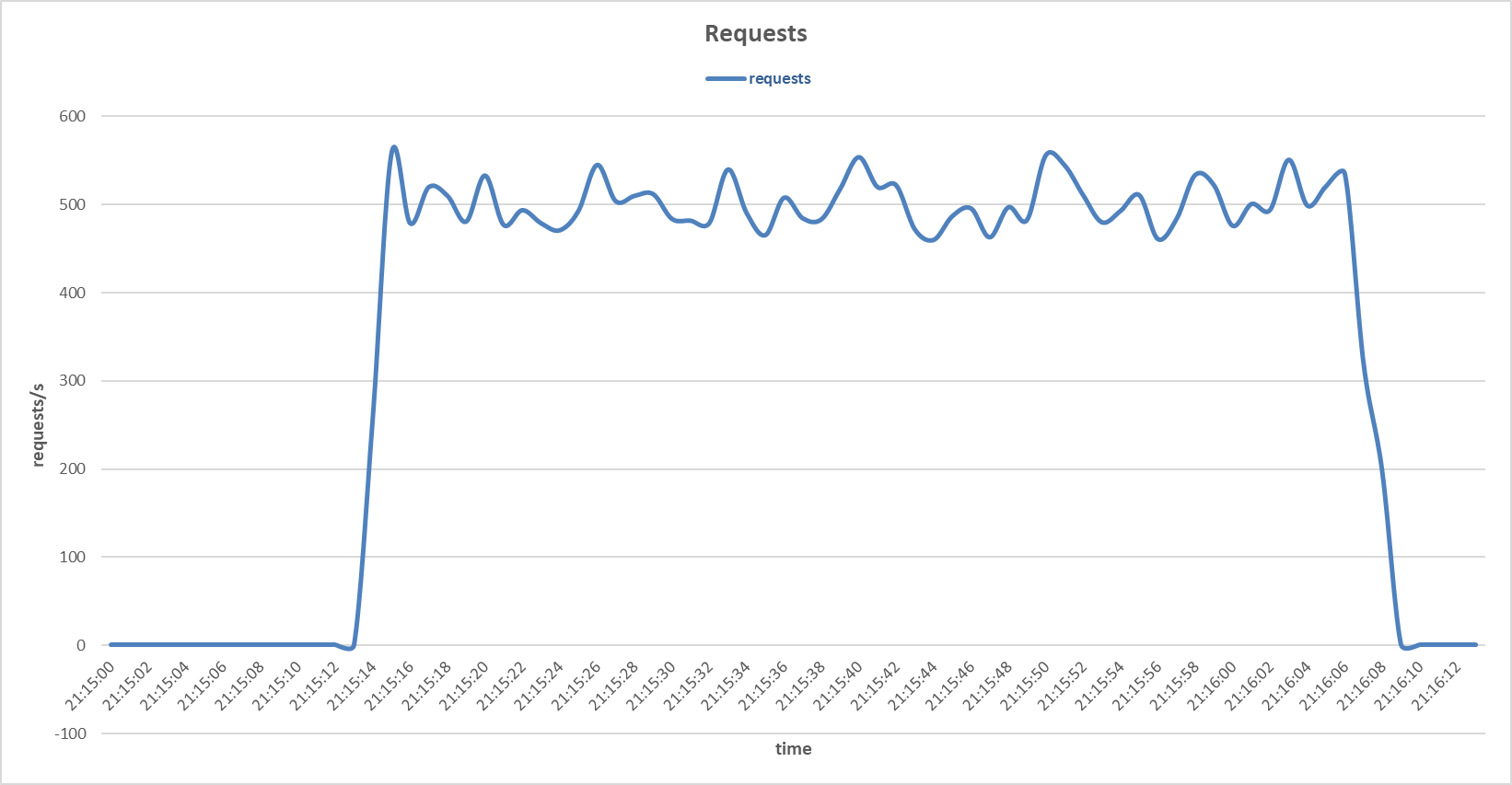
Requests to the secondary server during Bad TCP flags (All Flags Set) attack with Random Forest sensor.
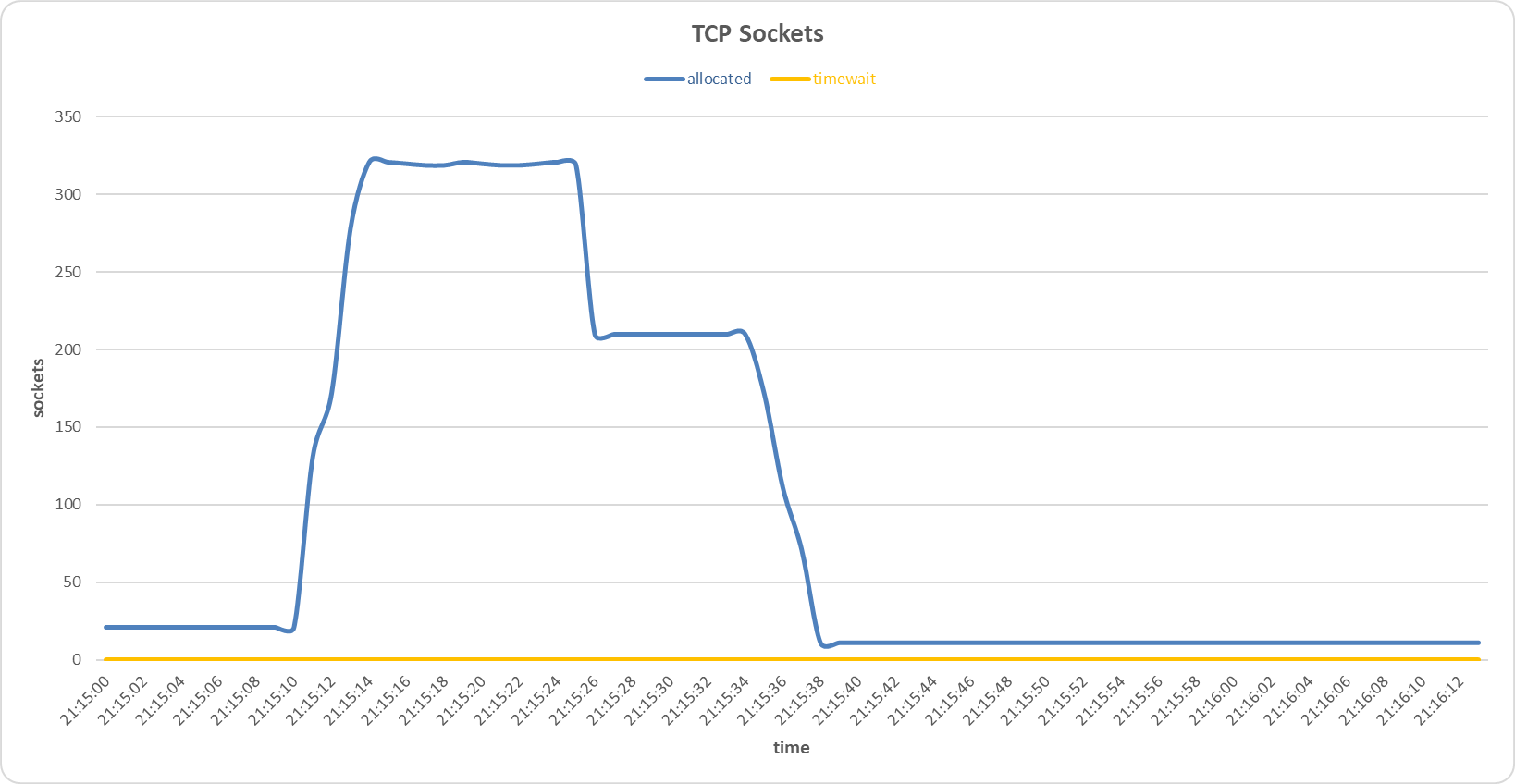
Sockets allocated and timewait on the primary server during Bad TCP flags (All Flags Set) attack with Random Forest sensor..
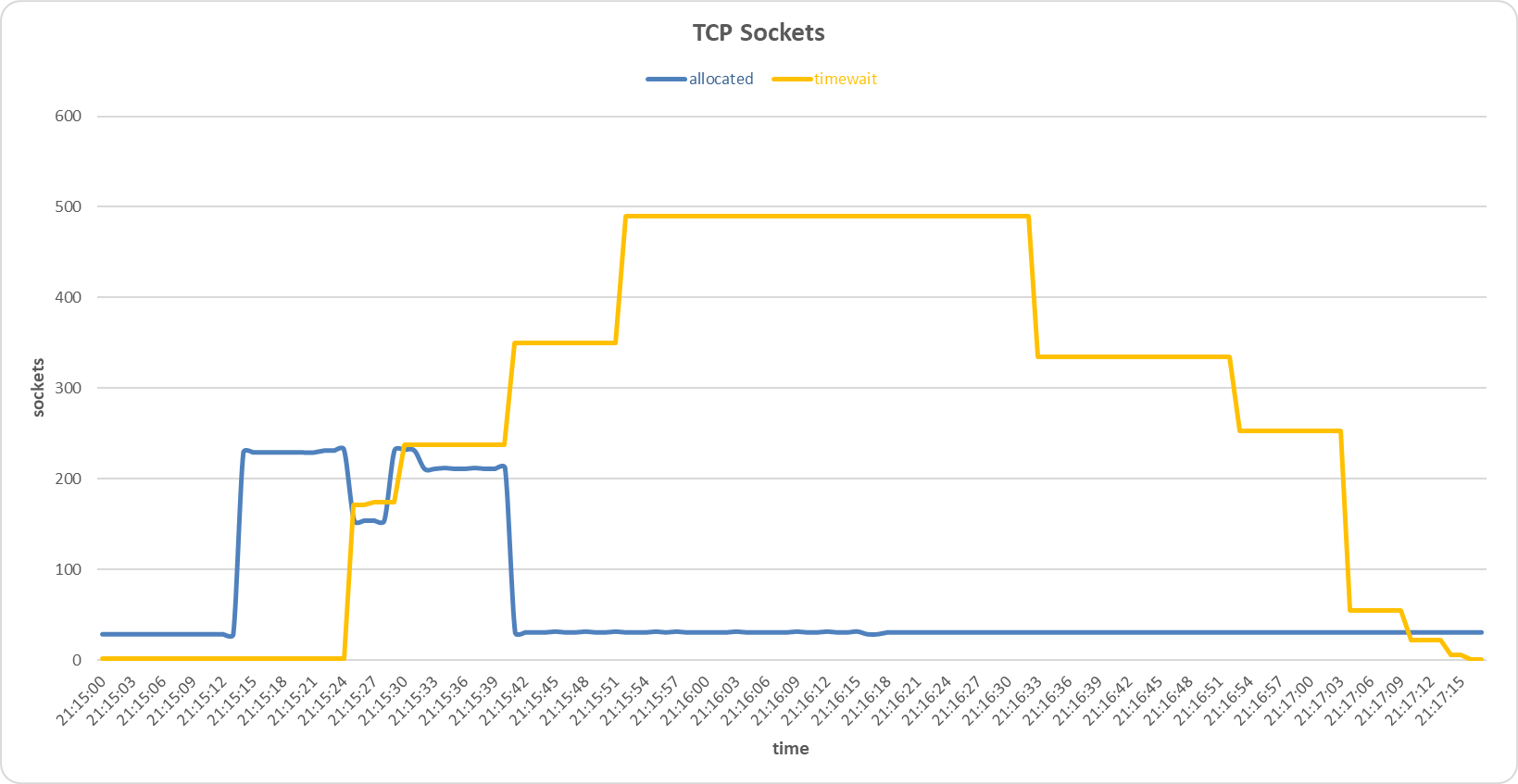
Sockets allocated and timewait on the secondary server during Bad TCP flags (All Flags Set) attack with Random Forest sensor.
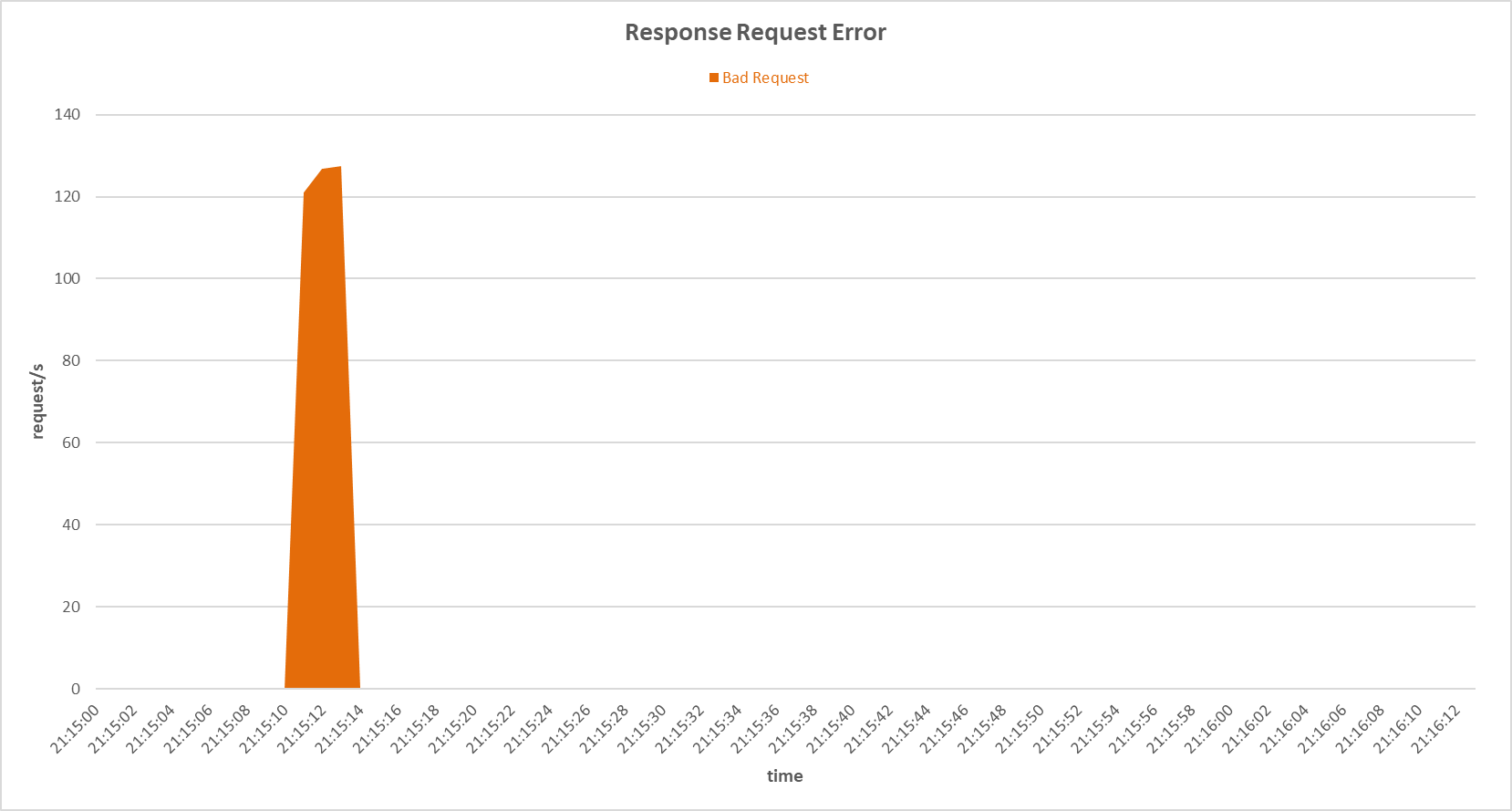
Request errors occurred on the primary server during Bad TCP flags (All Flags Set) attack with Random Forest sensor.
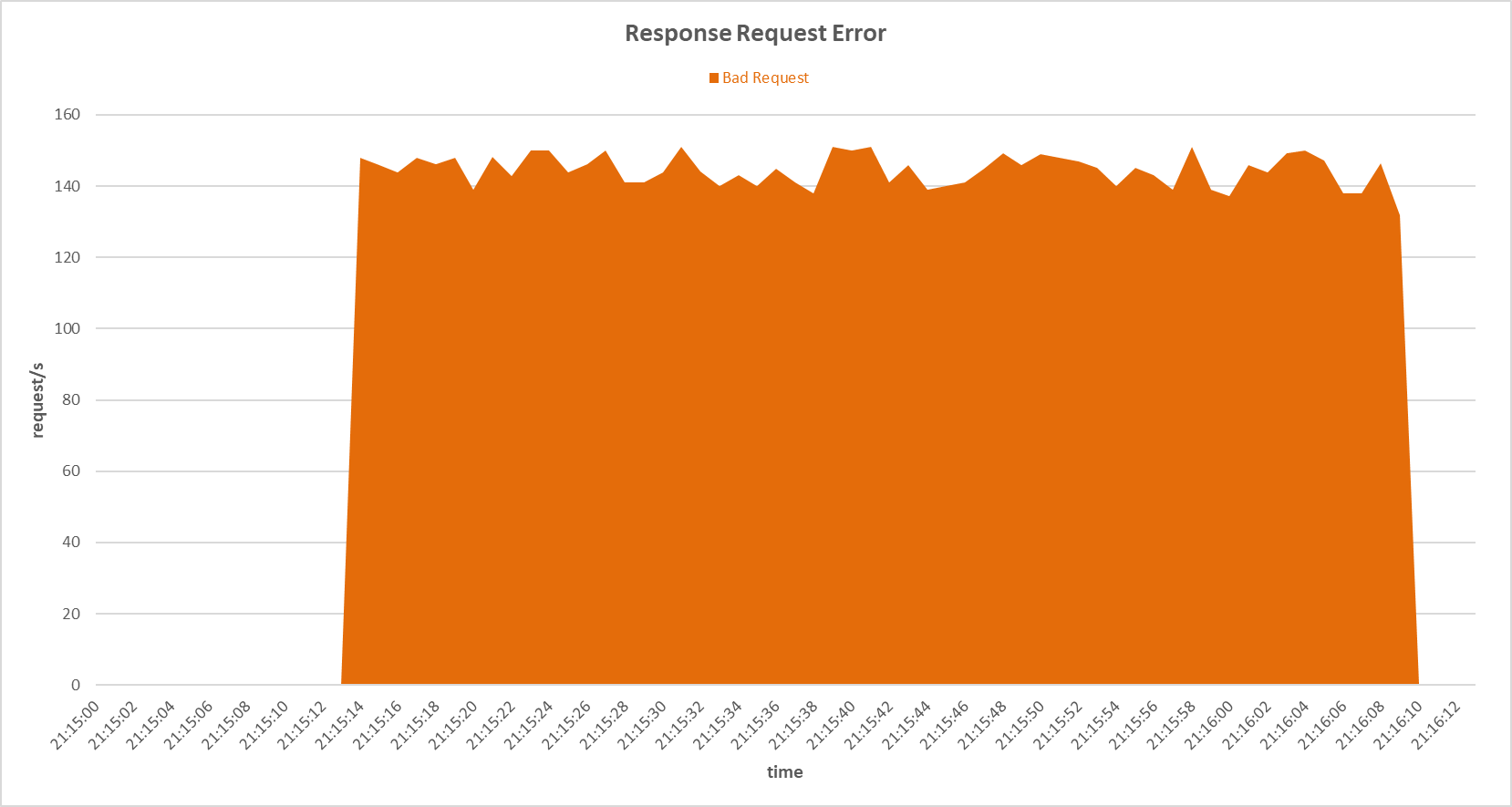
Request errors occurred on the secondary server during Bad TCP flags (All Flags Set) attack with Random Forest sensor.
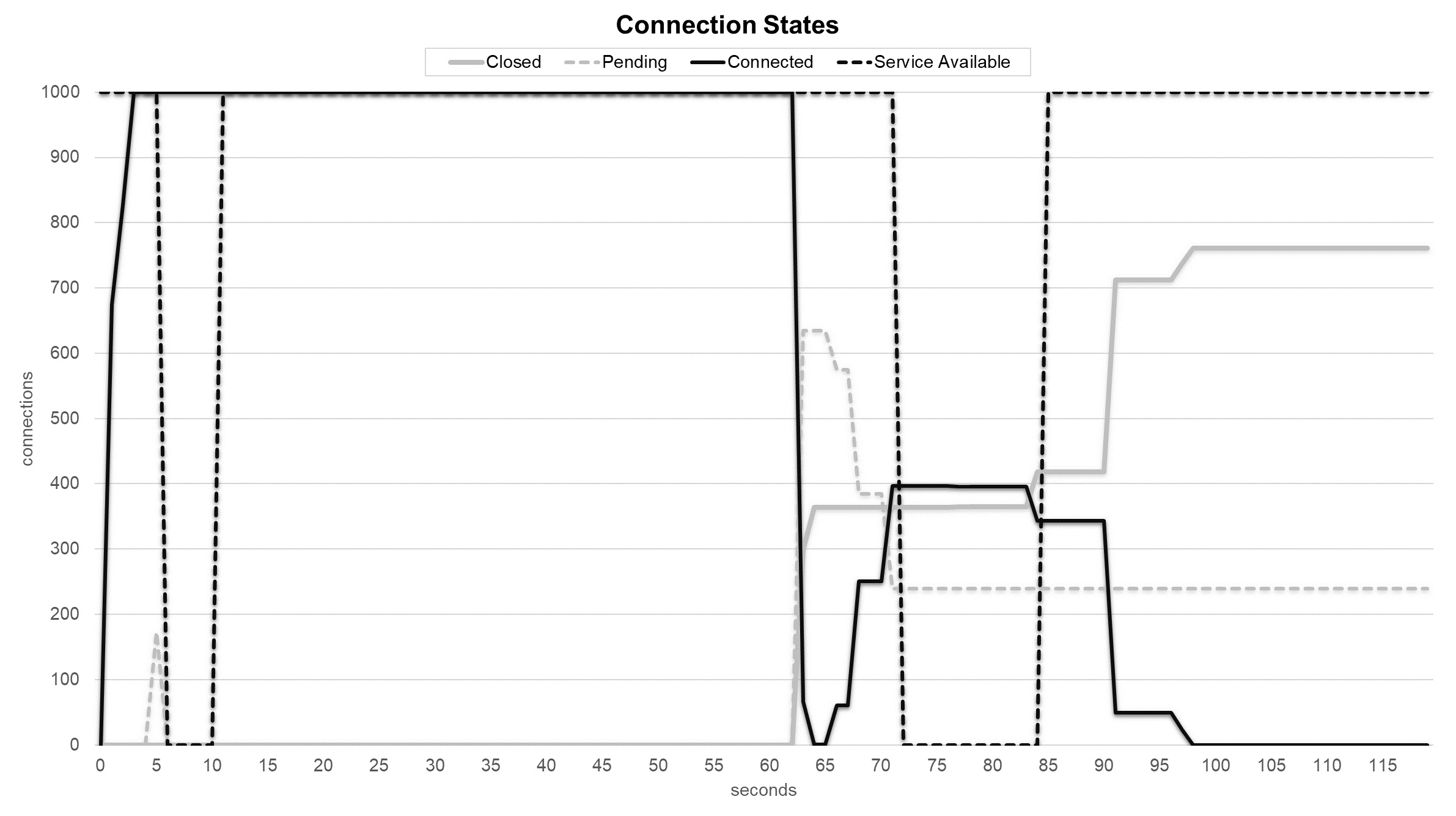
Service and connection states during Bad TCP flags (All Flags Set) attack with Random Forest sensor.
ATTACK FIN ONLY SET WITH GAUSSIAN NAIVE BAYES
Graph data: CVS File
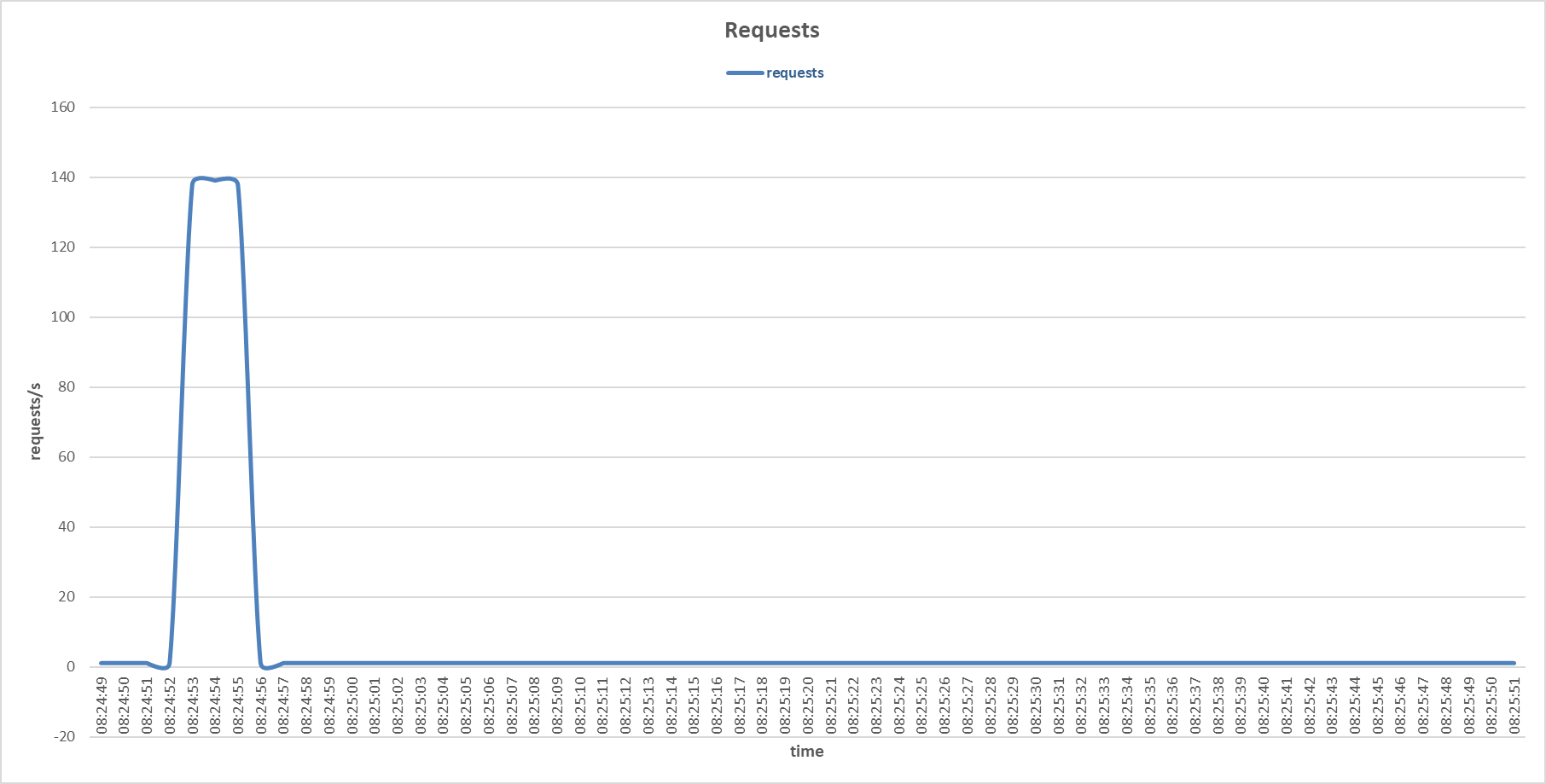
Requests to the primary server during FIN Only Set attack with Gaussian Naive Bayes sensor.
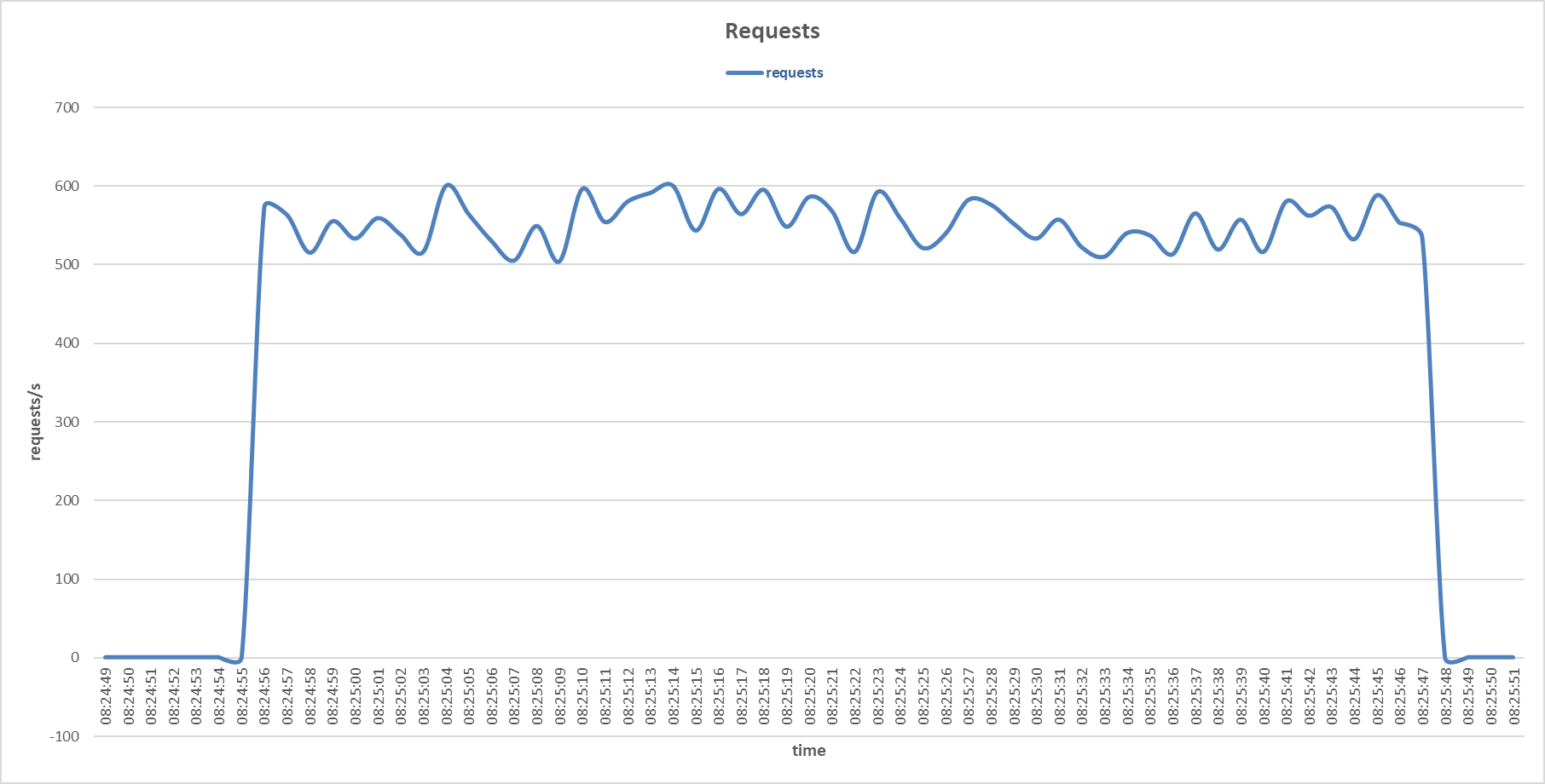
Requests to the secondary server during FIN Only Set attack with Gaussian Naive Bayes sensor.
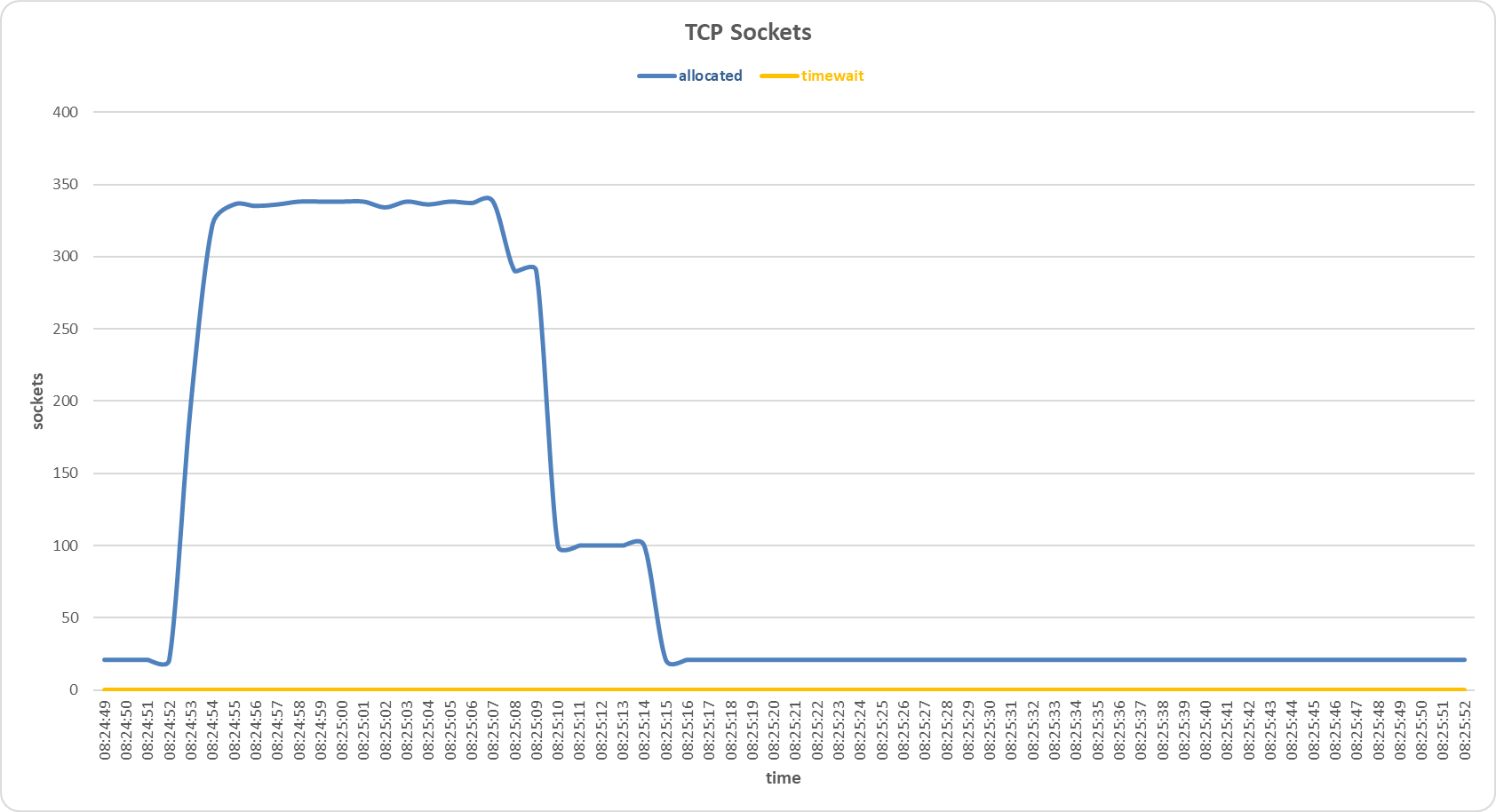
Sockets allocated and timewait on the primary server during FIN Only Set attack with Gaussian Naive Bayes sensor.
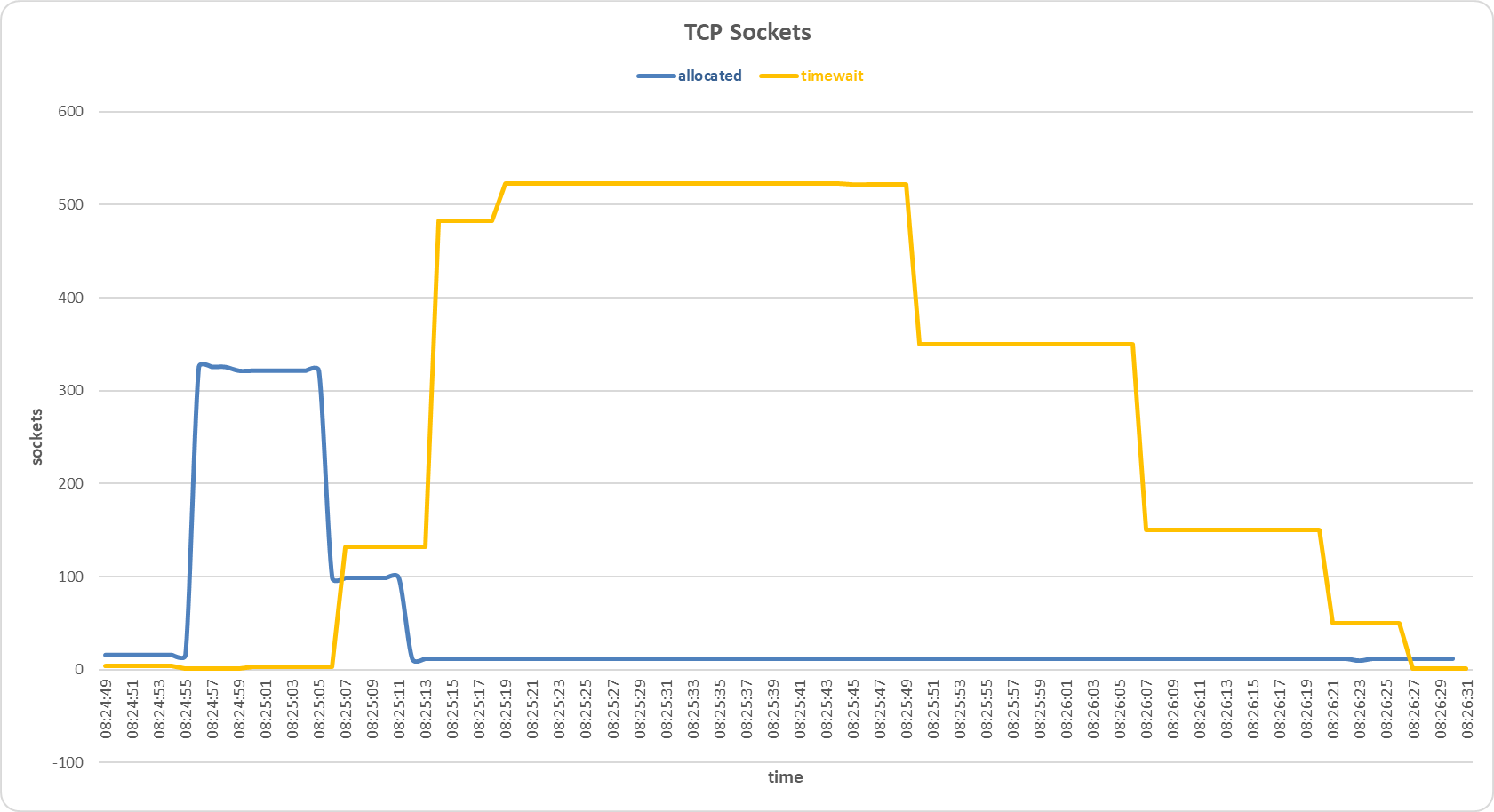
Sockets allocated and timewait on the secondary server during FIN Only Set attack with Random Forest sensor.
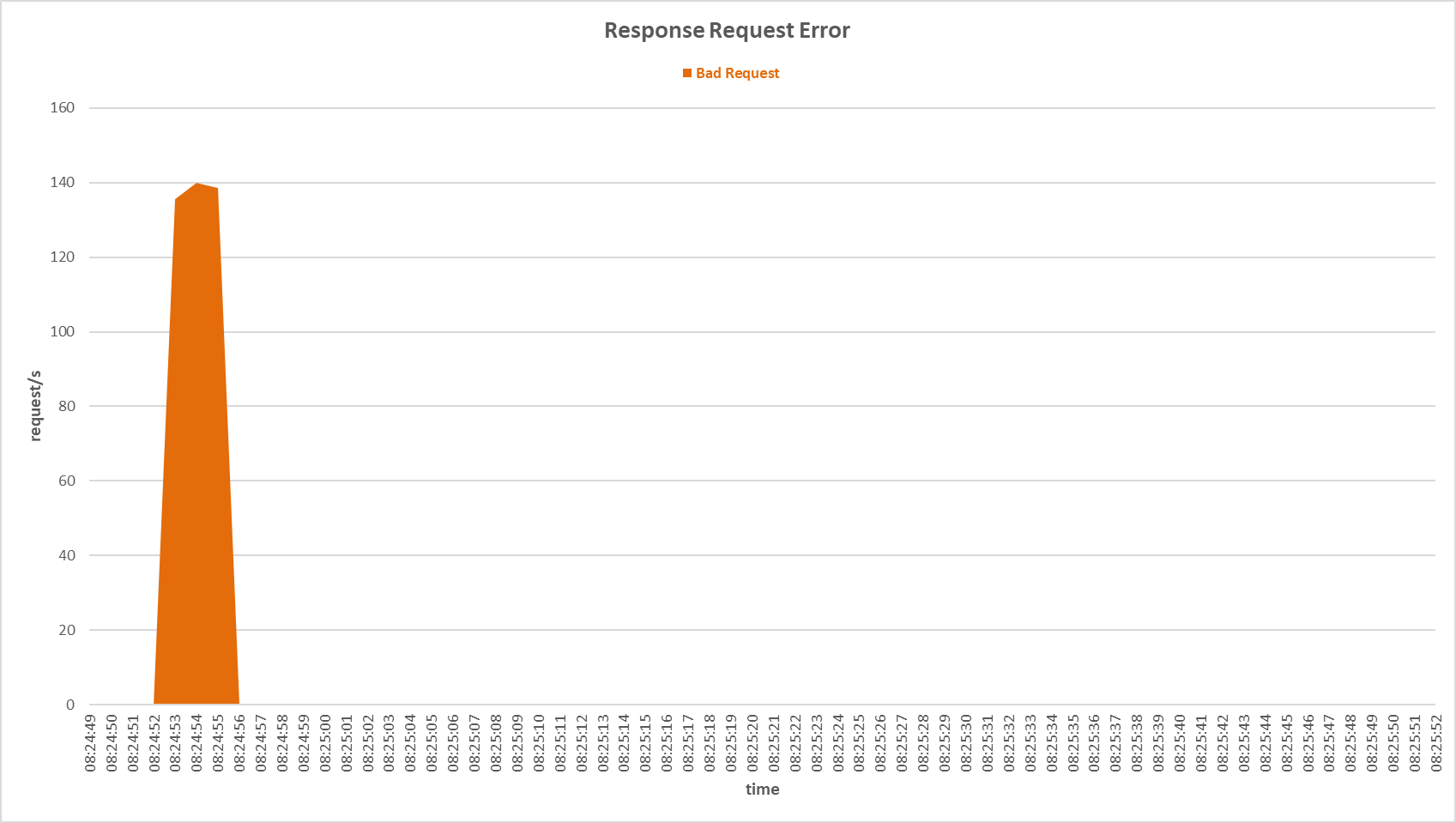
Request errors occurred on the primary server during FIN Only Set attack with Gaussian Naive Bayes sensor.
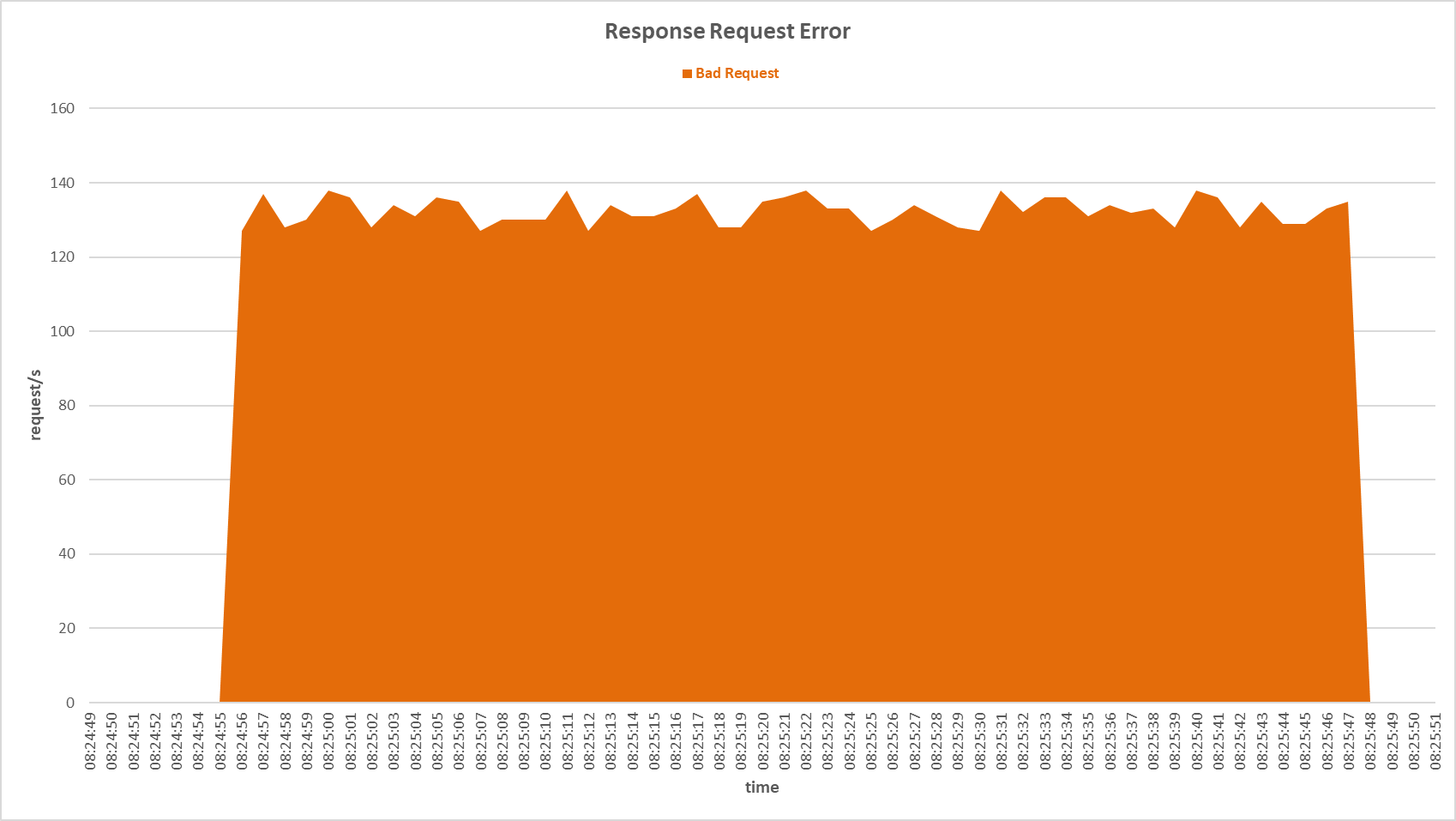
Request errors occurred on the secondary server during FIN Only Set attack with Gaussian Naive Bayes sensor.
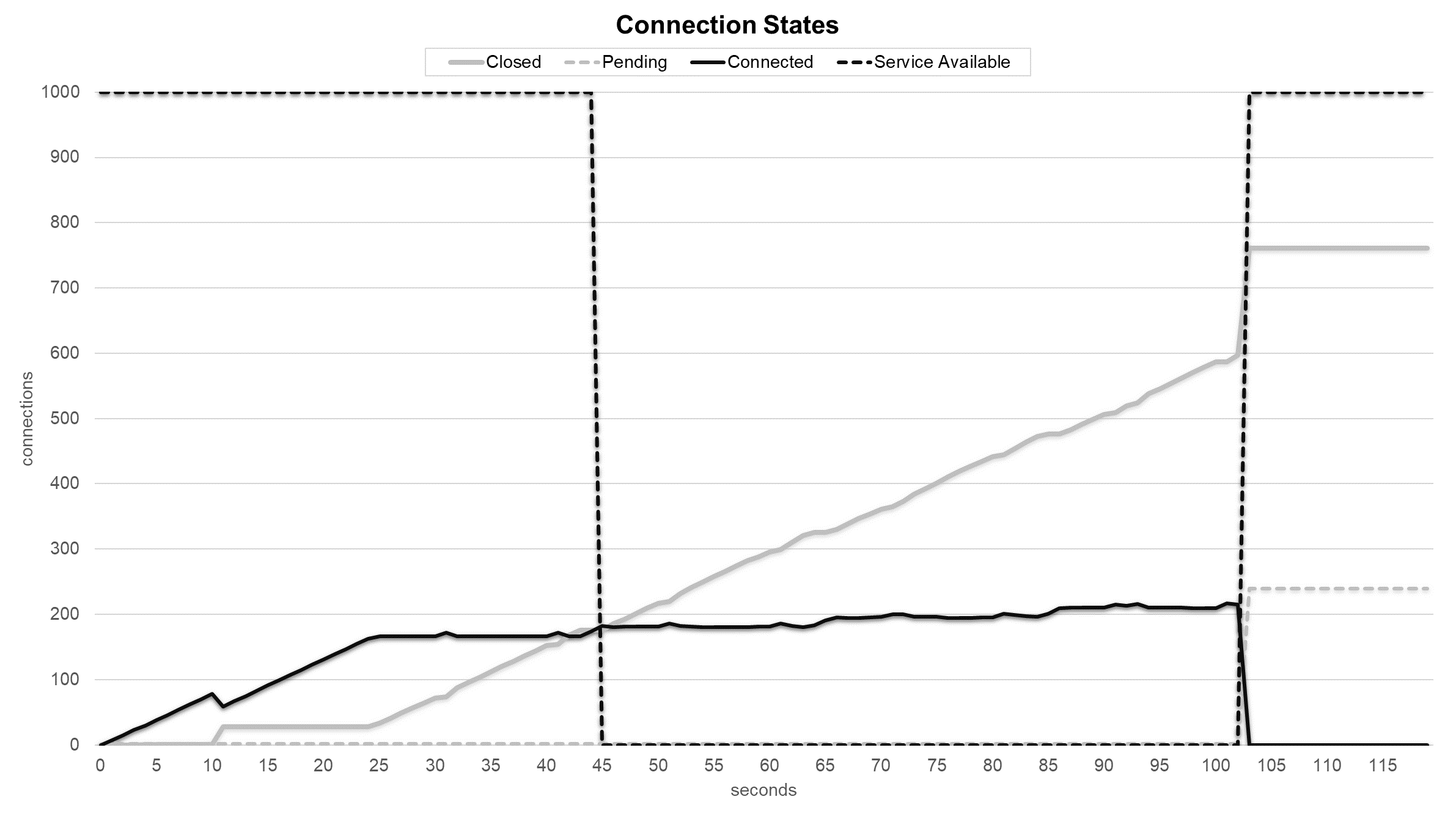
Service and connection states during FIN Only Set attack with Gaussian Naive Bayes sensor.
ATTACK SLOW HTTP POST WITH STACKING CLASSIFIER
Graph data: CVS File
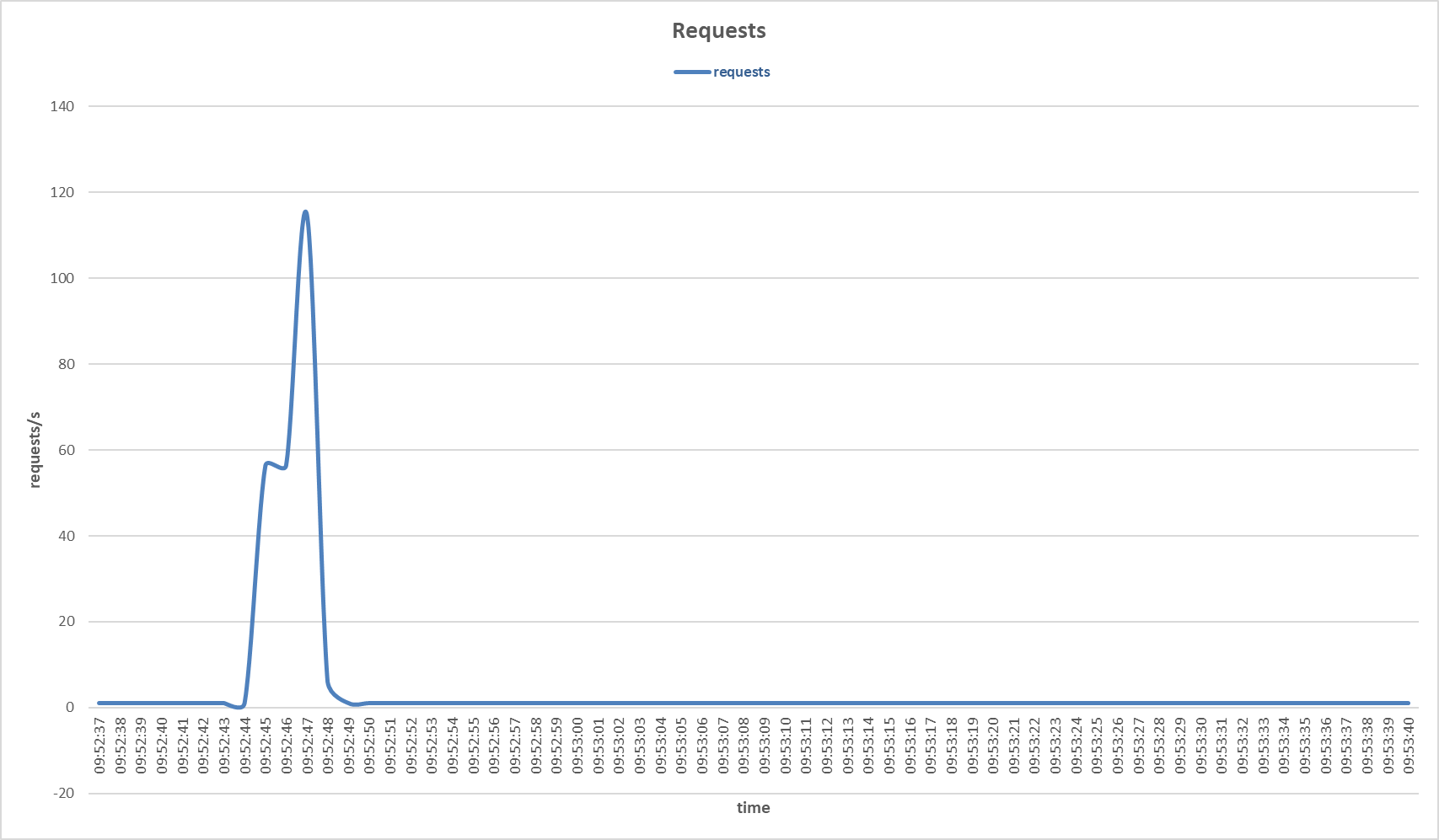
Requests to the primary server during Slow HTTP POST attack with Stacking Classifier sensor.
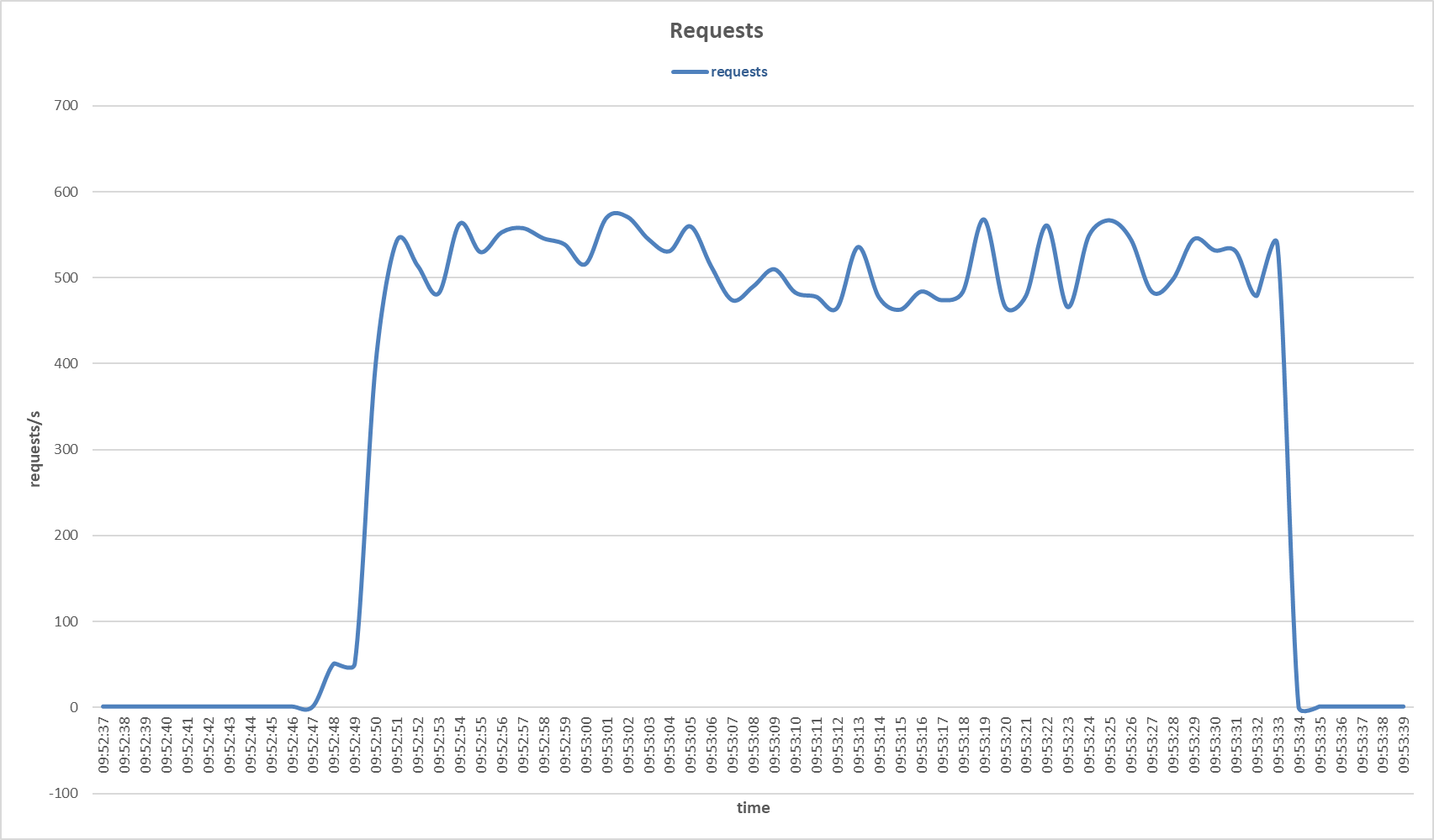
Requests to the secondary server during Slow HTTP POST attack with Stacking Classifier sensor.
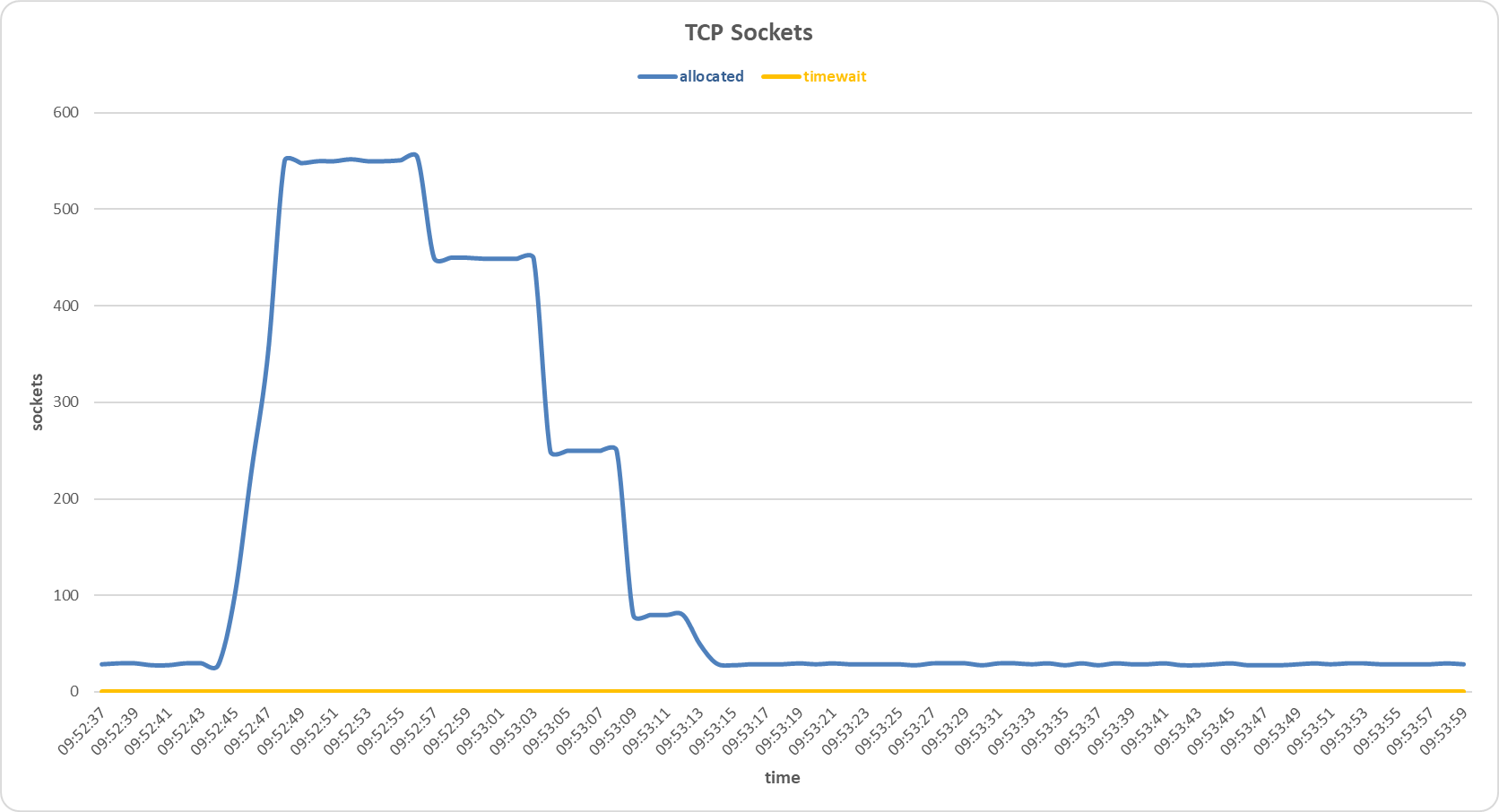
Sockets allocated and timewait on the primary server during Slow HTTP POST attack with Stacking Classifier sensor.
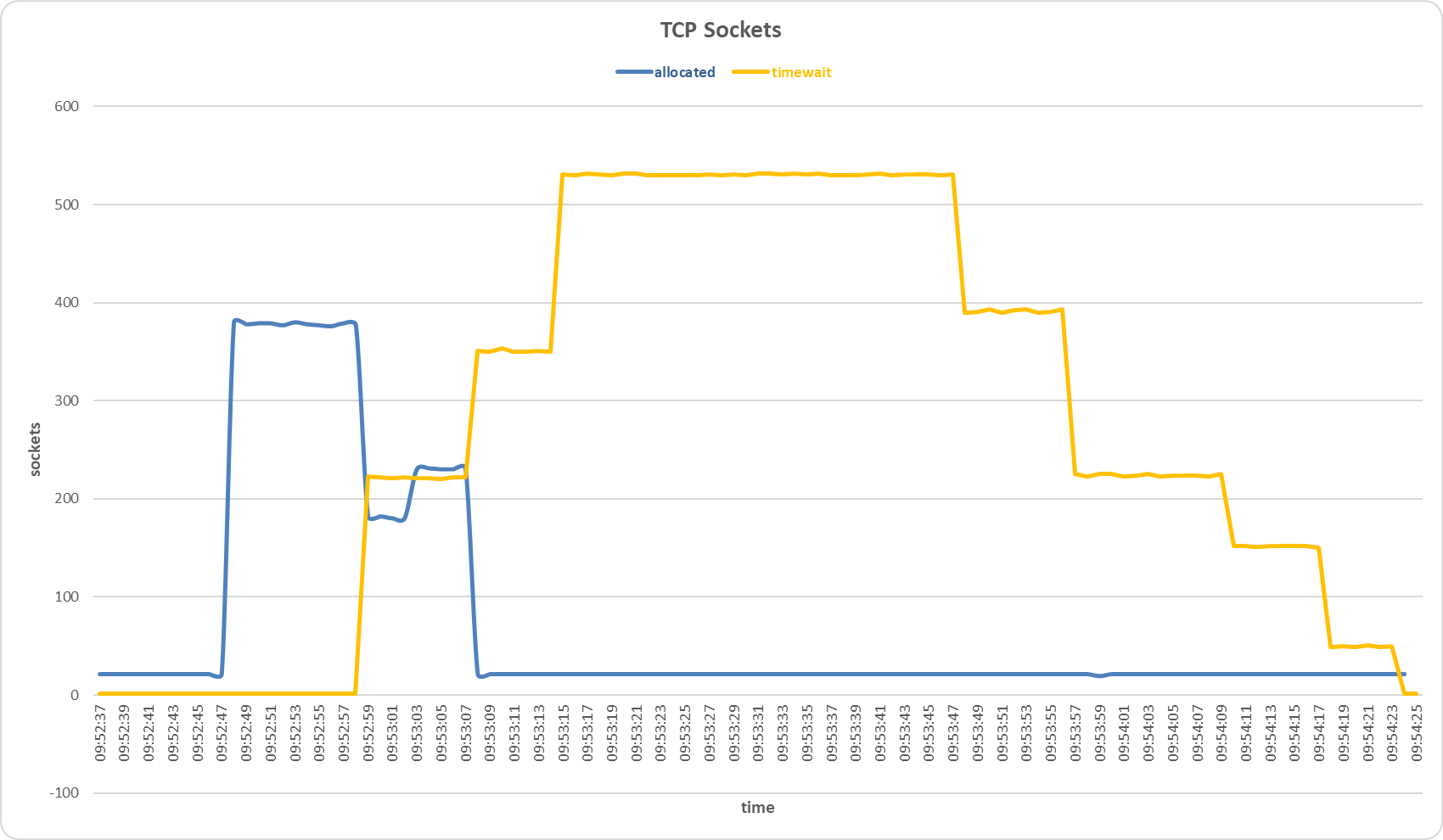
Sockets allocated and timewait on the secondary server during Slow HTTP POST attack with Stacking Classifier sensor.
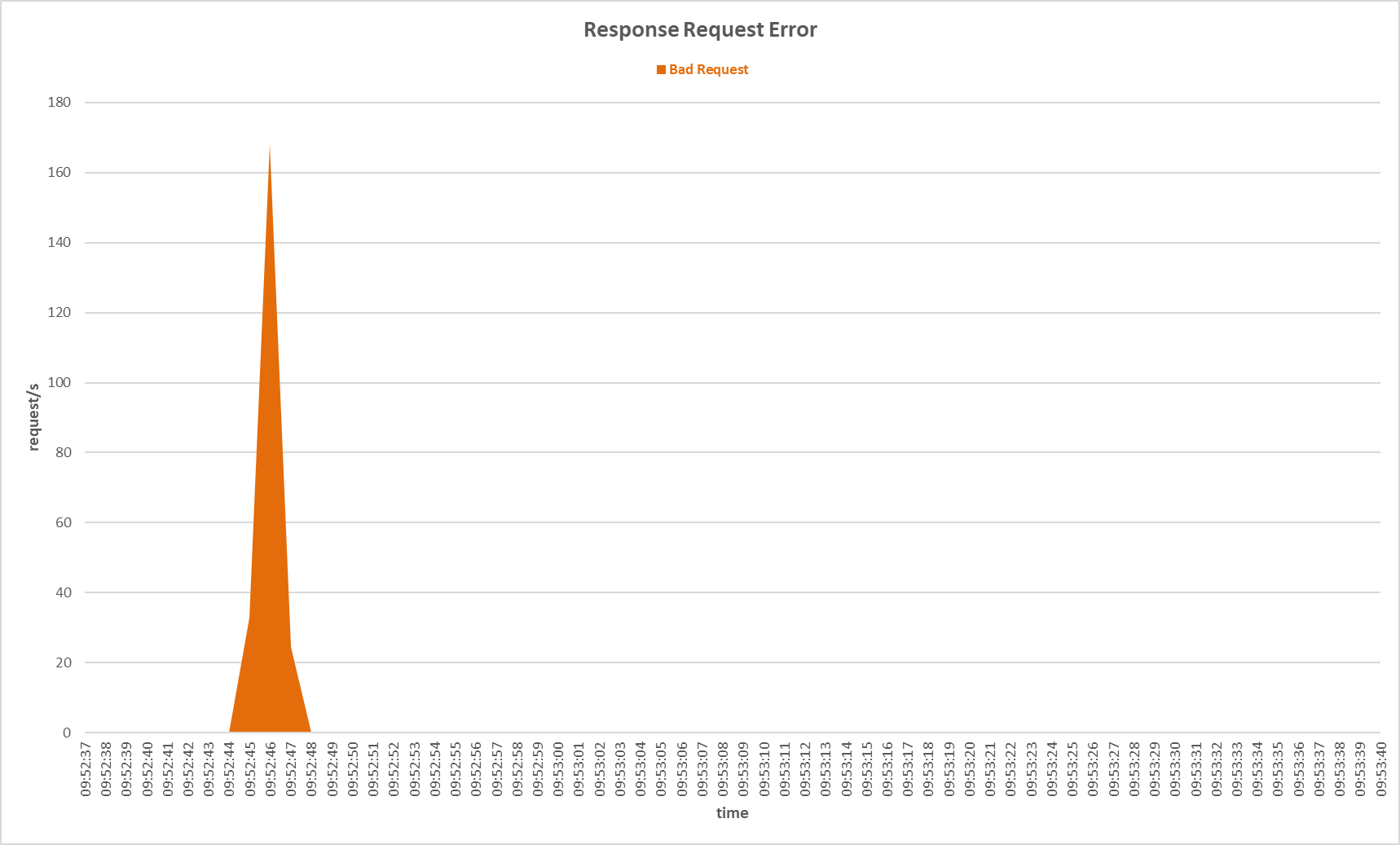
Request errors occurred on the primary server during Slow HTTP POST attack with Stacking Classifier sensor.
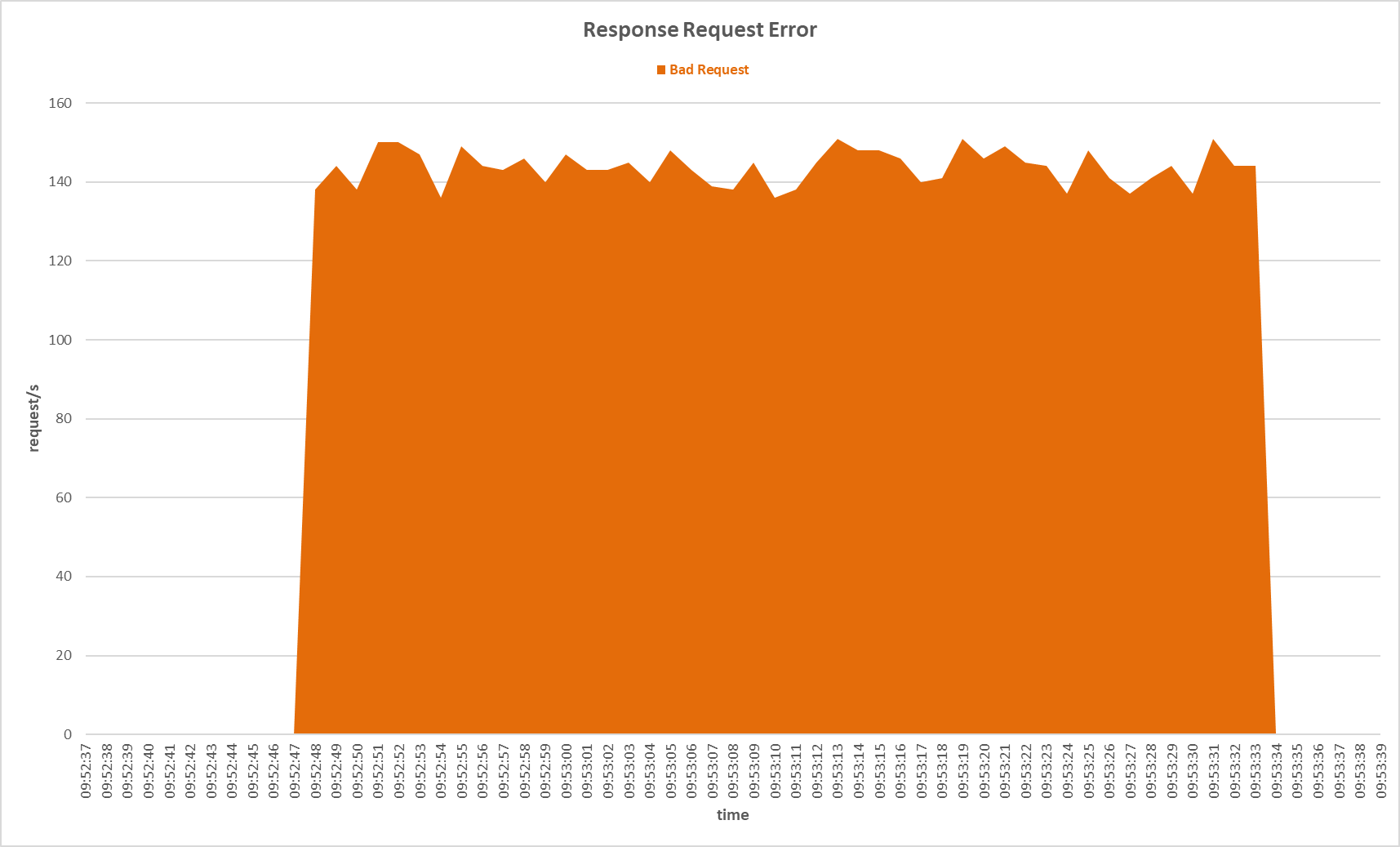
Request errors occurred on the secondary server during Slow HTTP POST attack with Stacking Classifier sensor.
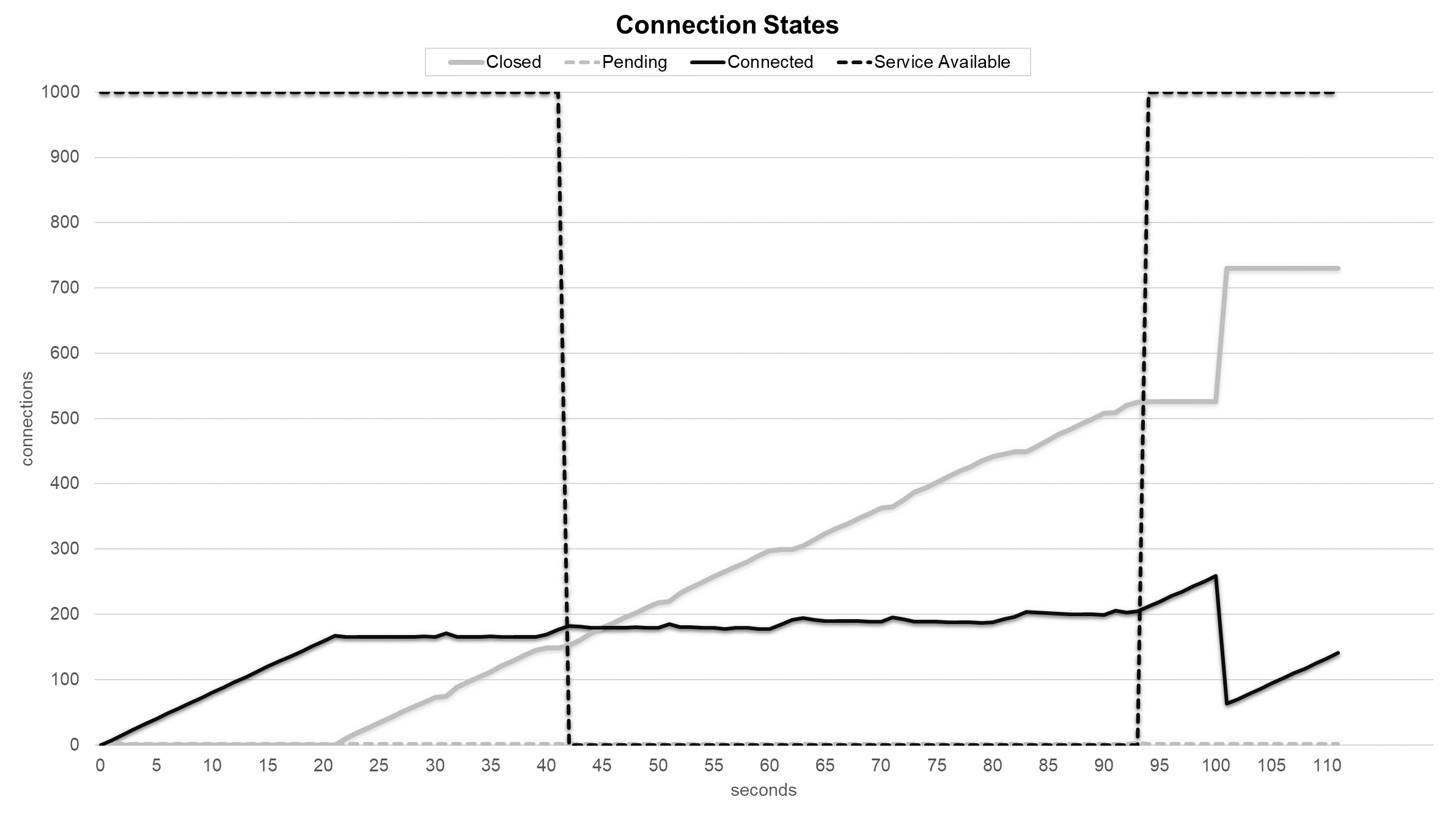
Service and connection states during Slow HTTP POST attack with Stacking Classifier sensor.
ATTACK SYN AND FIN SET WITH SUPPORT VECTOR SUPPORT VECTOR
Graph data: CVS File
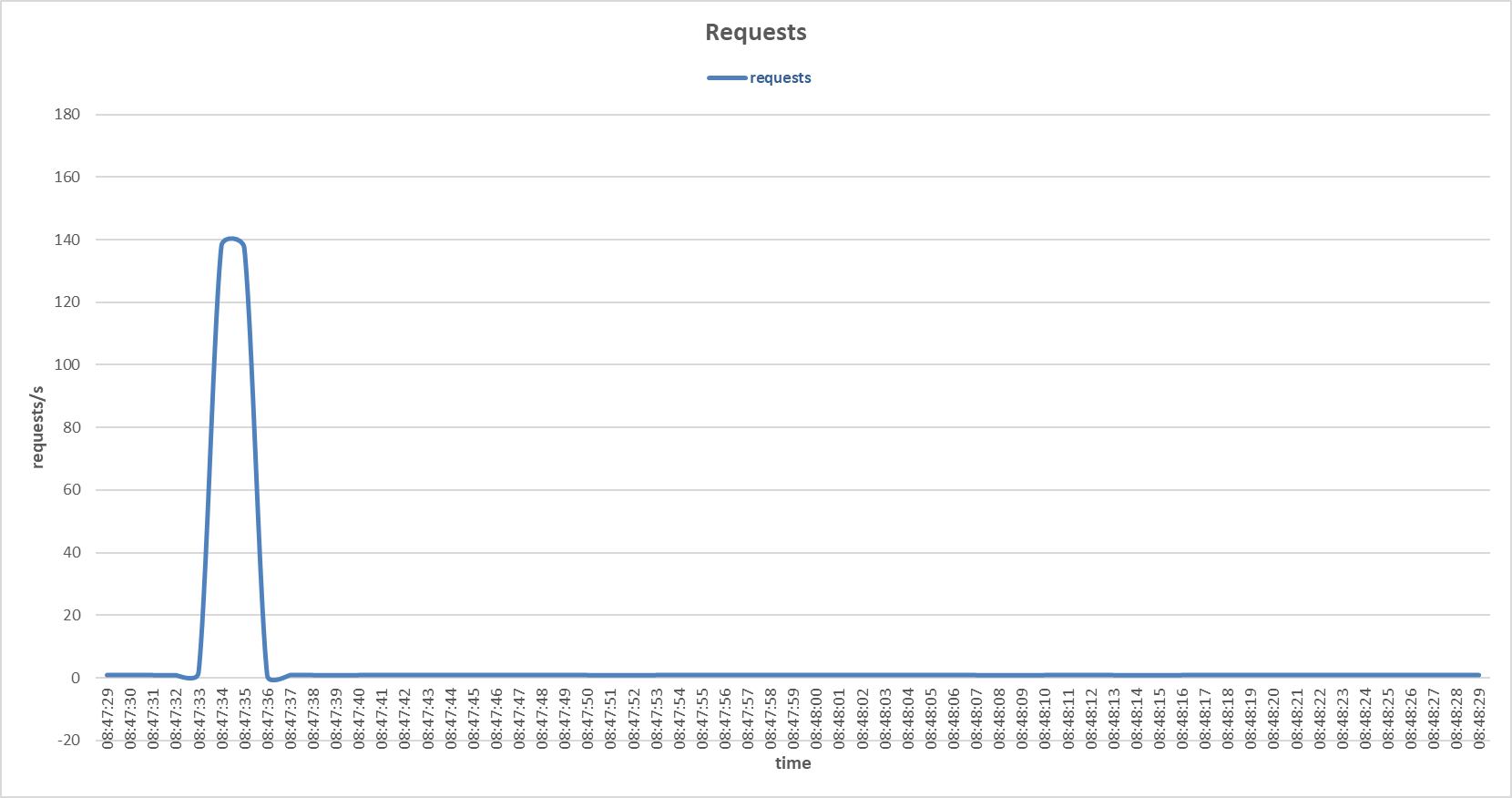
Requests to the primary server during SYN and FIN Set attack with Support Vector Machine sensor.
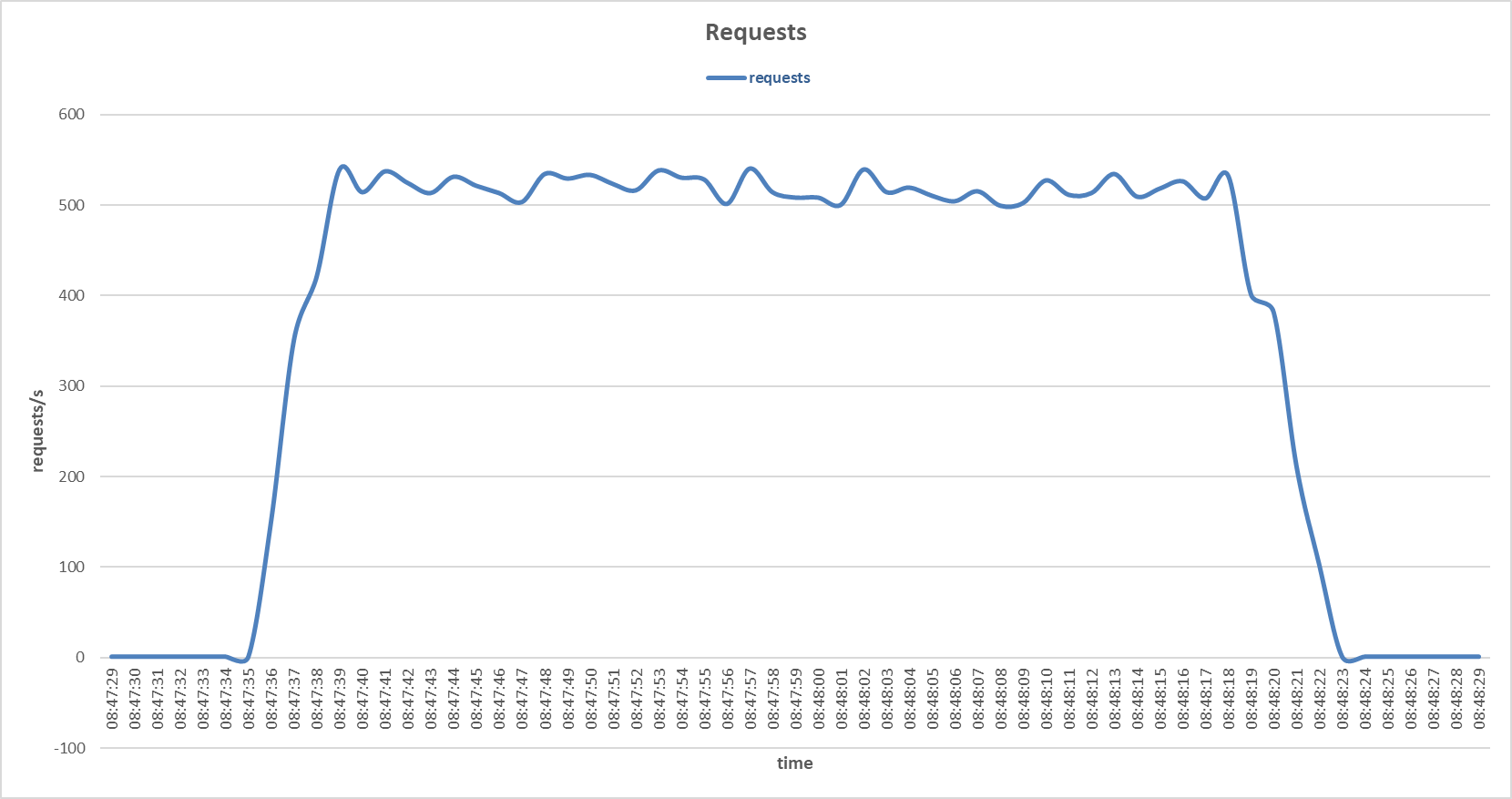
Requests to the secondary server during SYN and FIN Set attack with Support Vector Machine sensor.
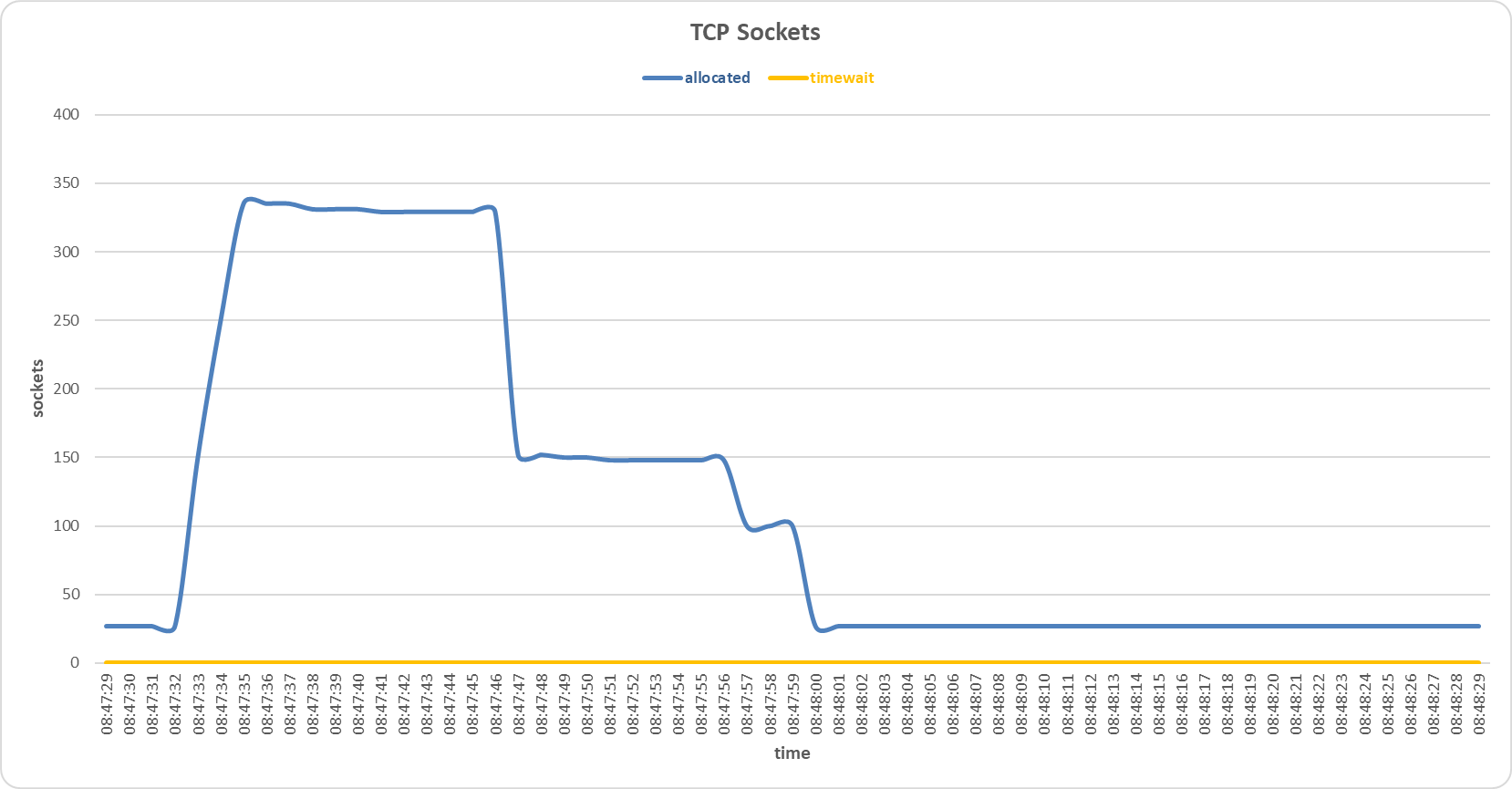
Sockets allocated and timewait on the primary server during SYN and FIN Set attack with Support Vector Machine sensor.
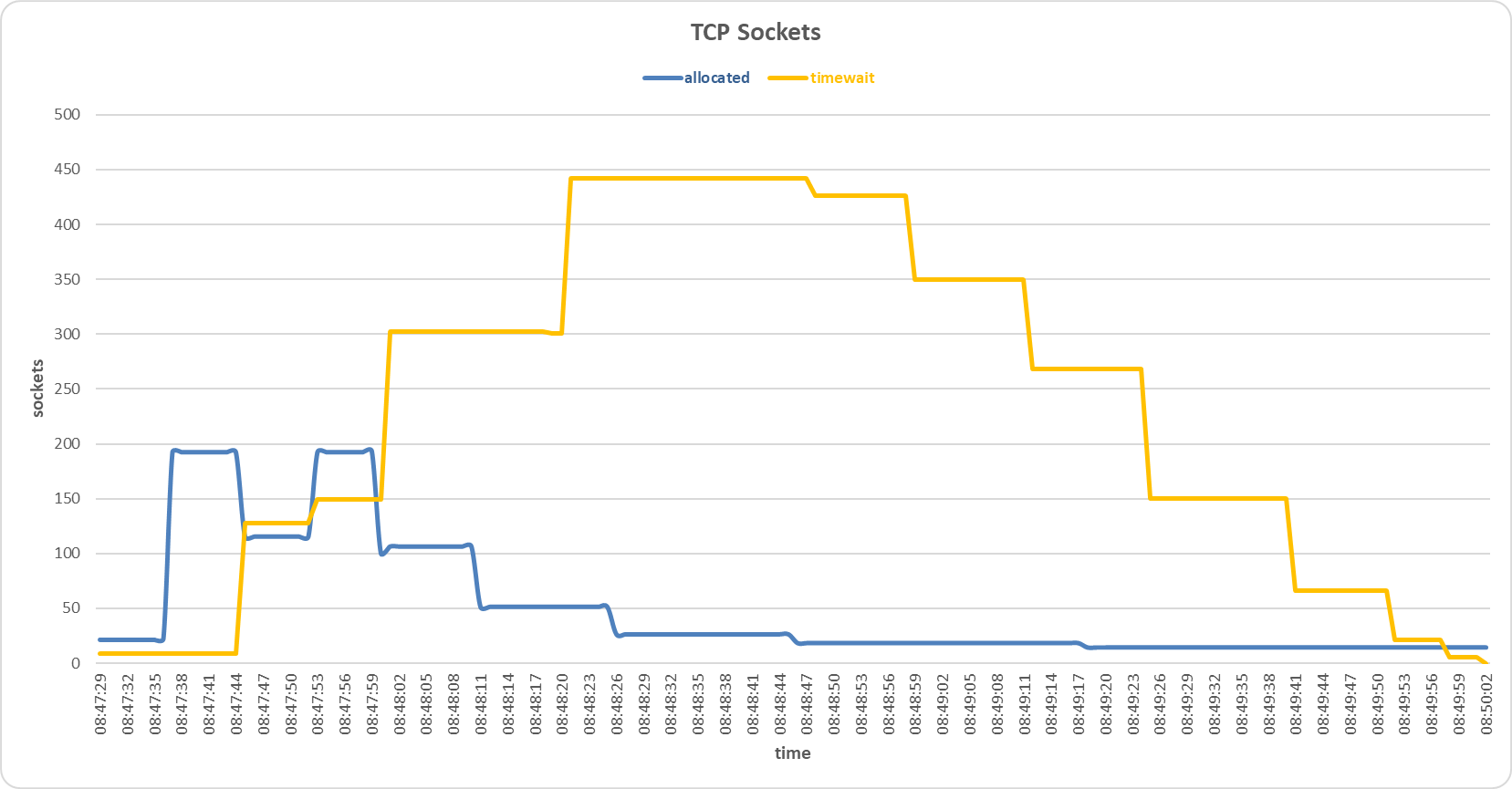
Sockets allocated and timewait on the secondary server during SYN and FIN Set attack with Support Vector Machine sensor.
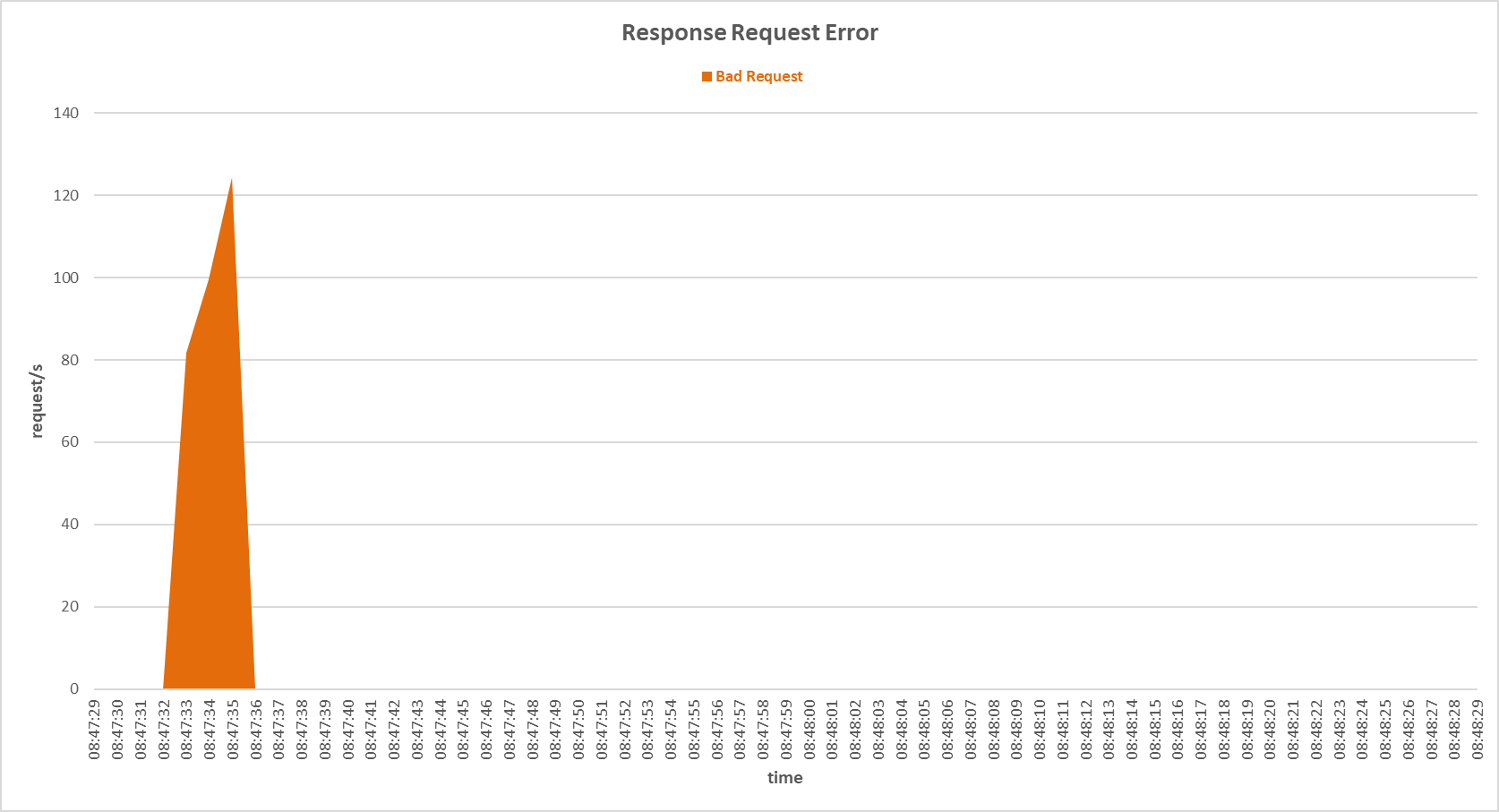
Request errors occurred on the primary server during SYN and FIN Set attack with Support Vector Machine sensor.
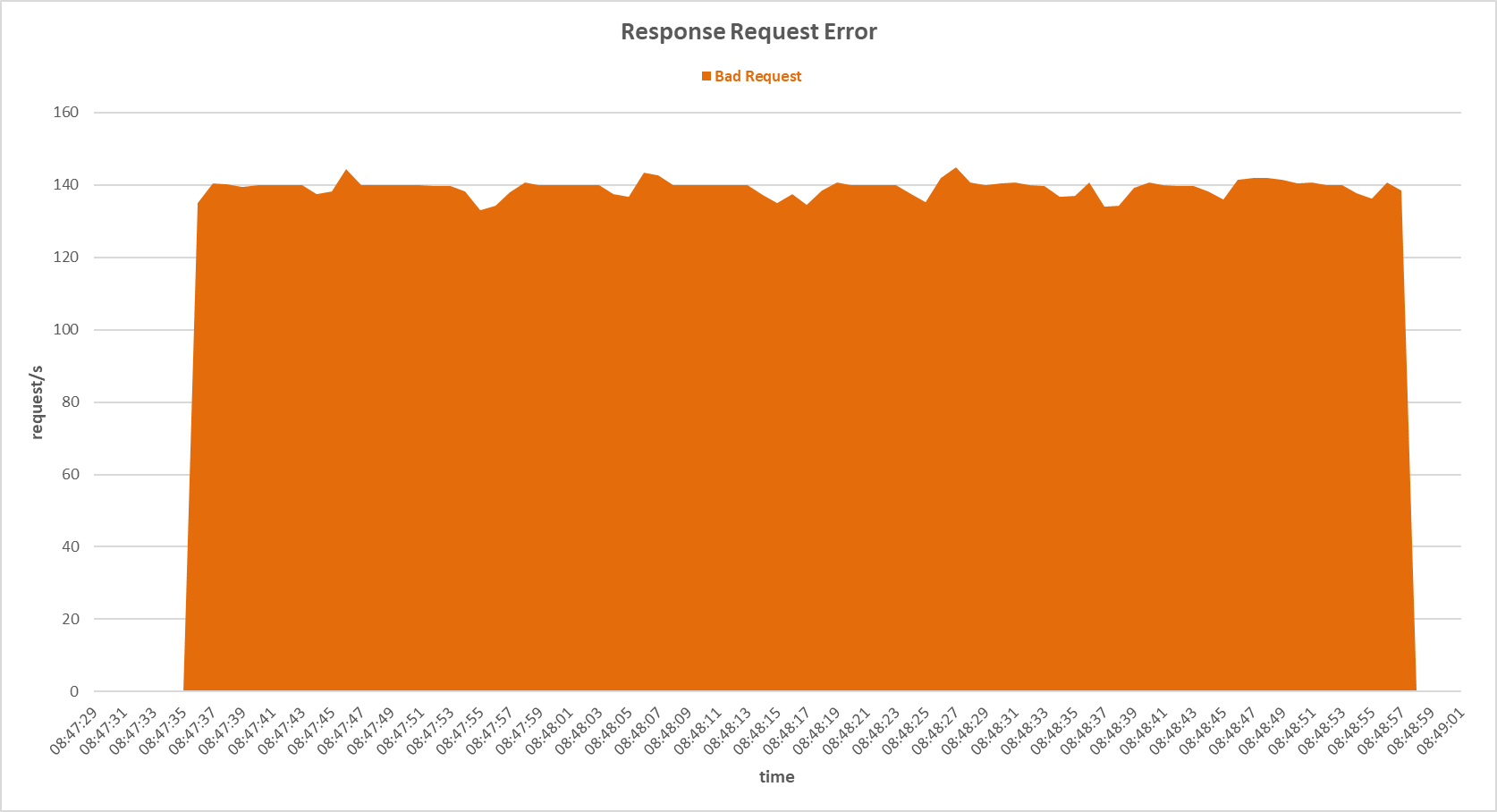
Request errors occurred on the secondary server during SYN and FIN Set attack with Support Vector Machine sensor.
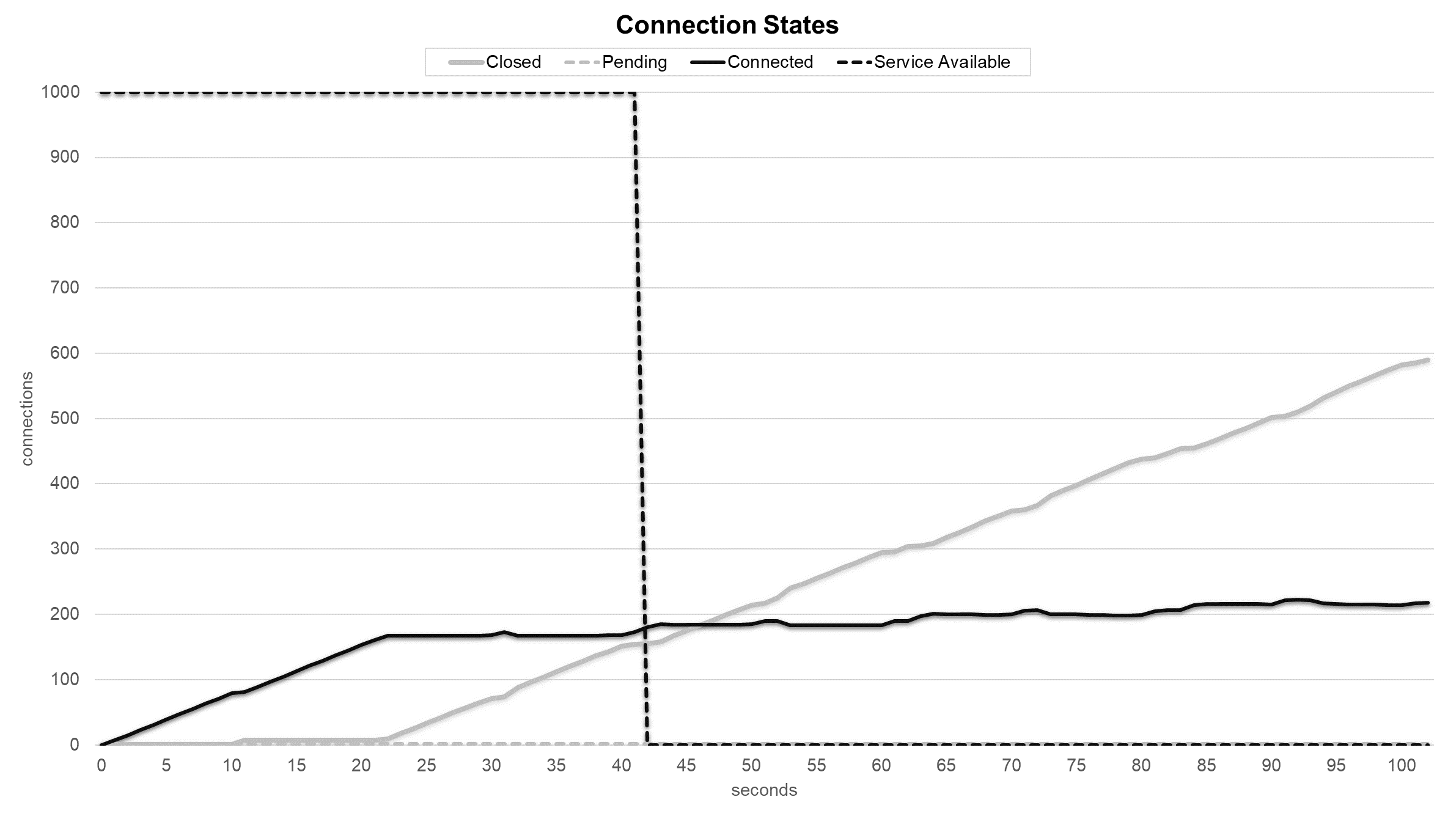
Service and connection states during SYN and FIN Set attack with Support Vector Machine sensor.
ATTACK TCP SYN FLOOD WITH MULTILAYER PERCEPTRON
Graph data: CVS File
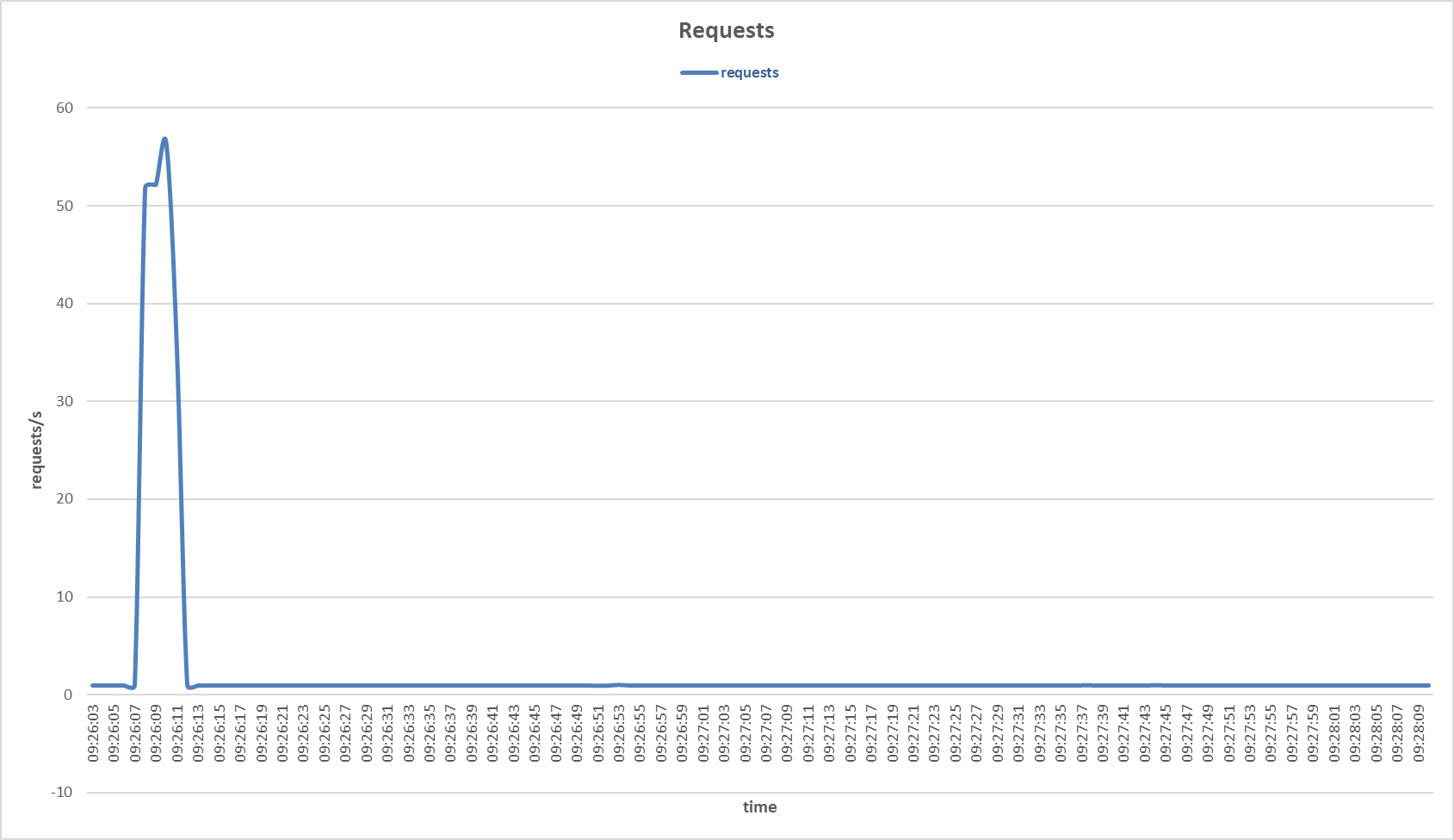
Requests to the primary server during TCP SYN Flood attack with Multilayer Perceptron sensor.
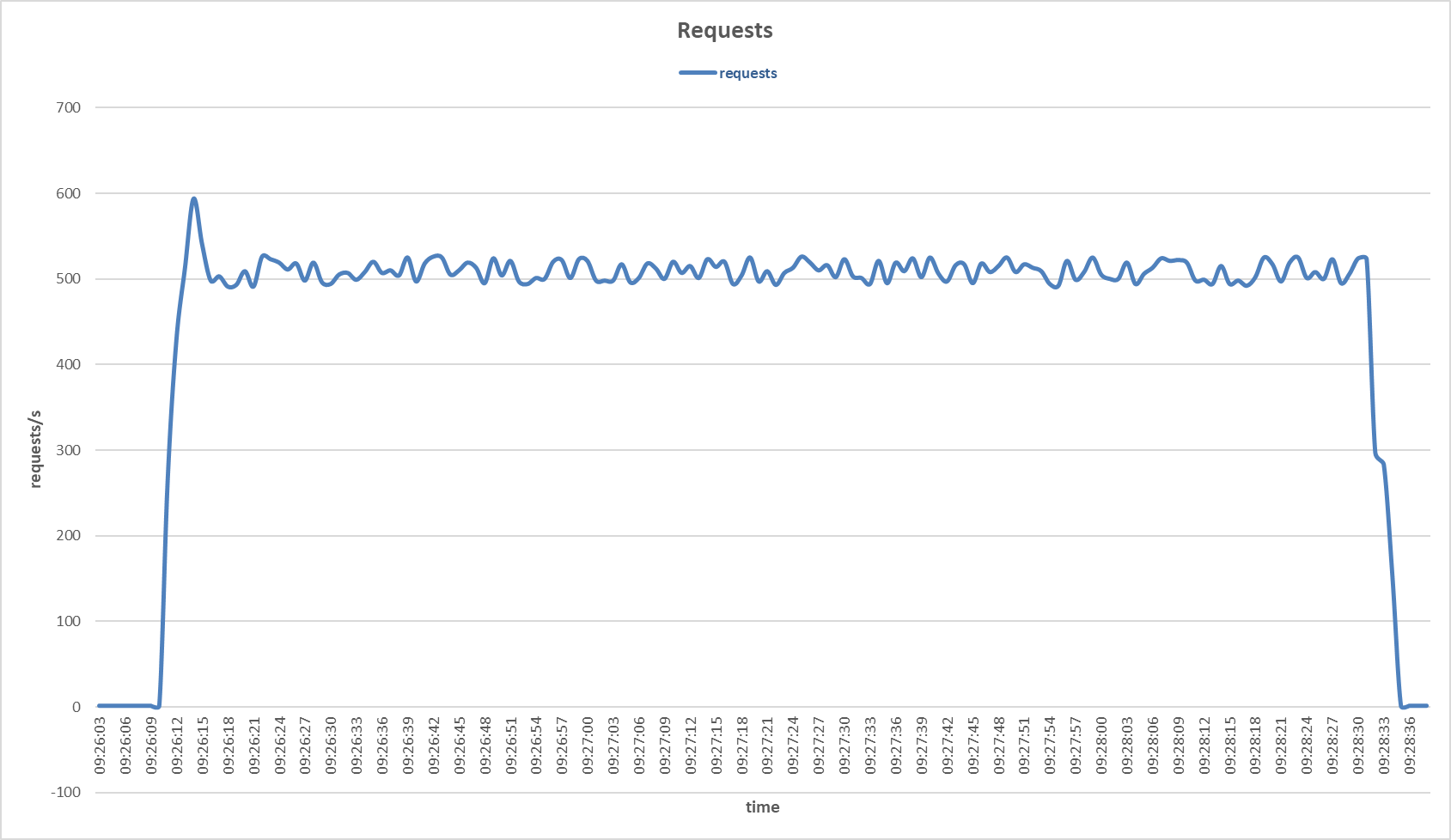
Requests to the secondary server during SYN and FIN Set attack with Multilayer Perceptron sensor.
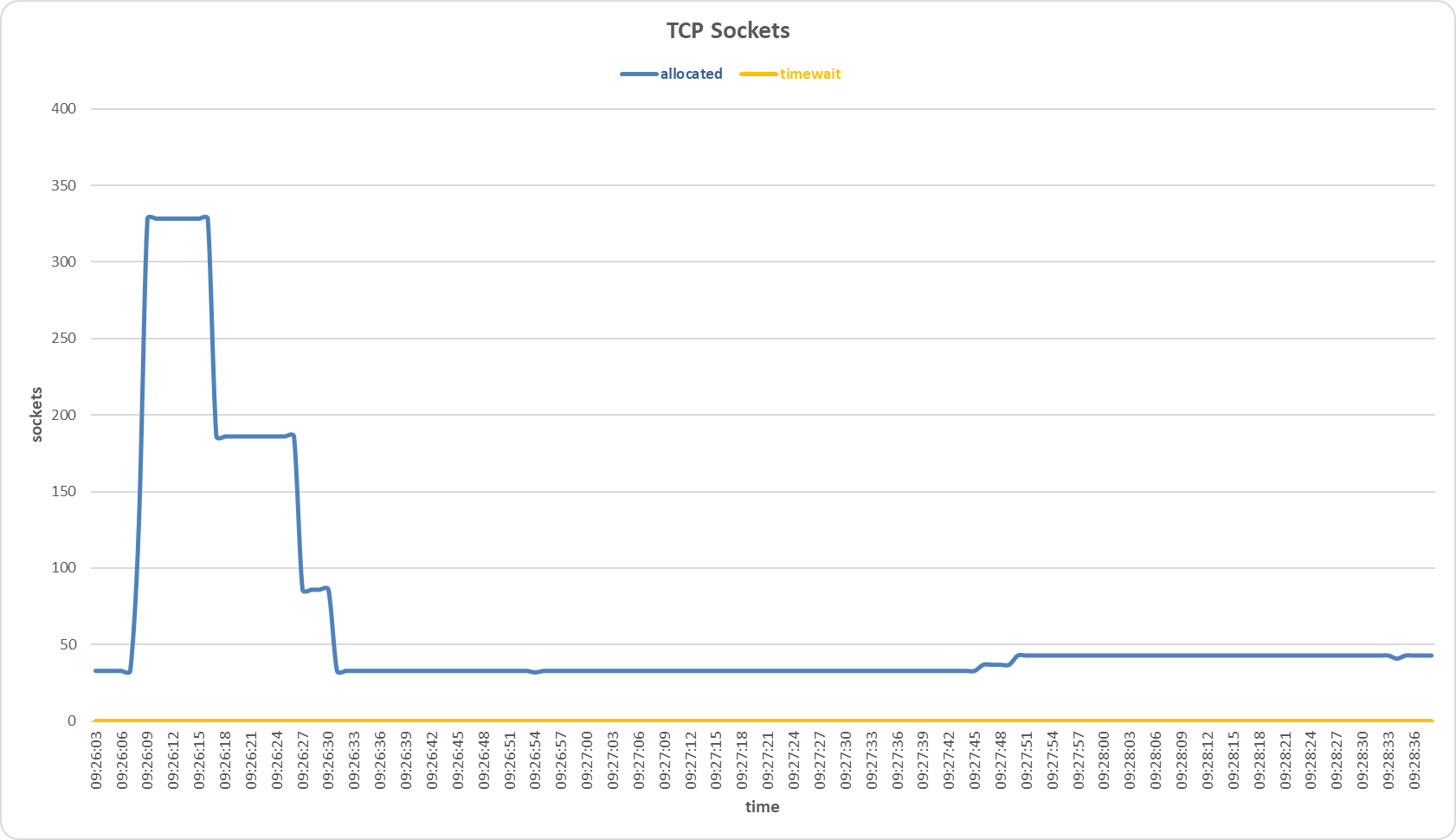
Sockets allocated and timewait on the primary server during TCP SYN Flood attack with Multilayer Perceptron sensor.
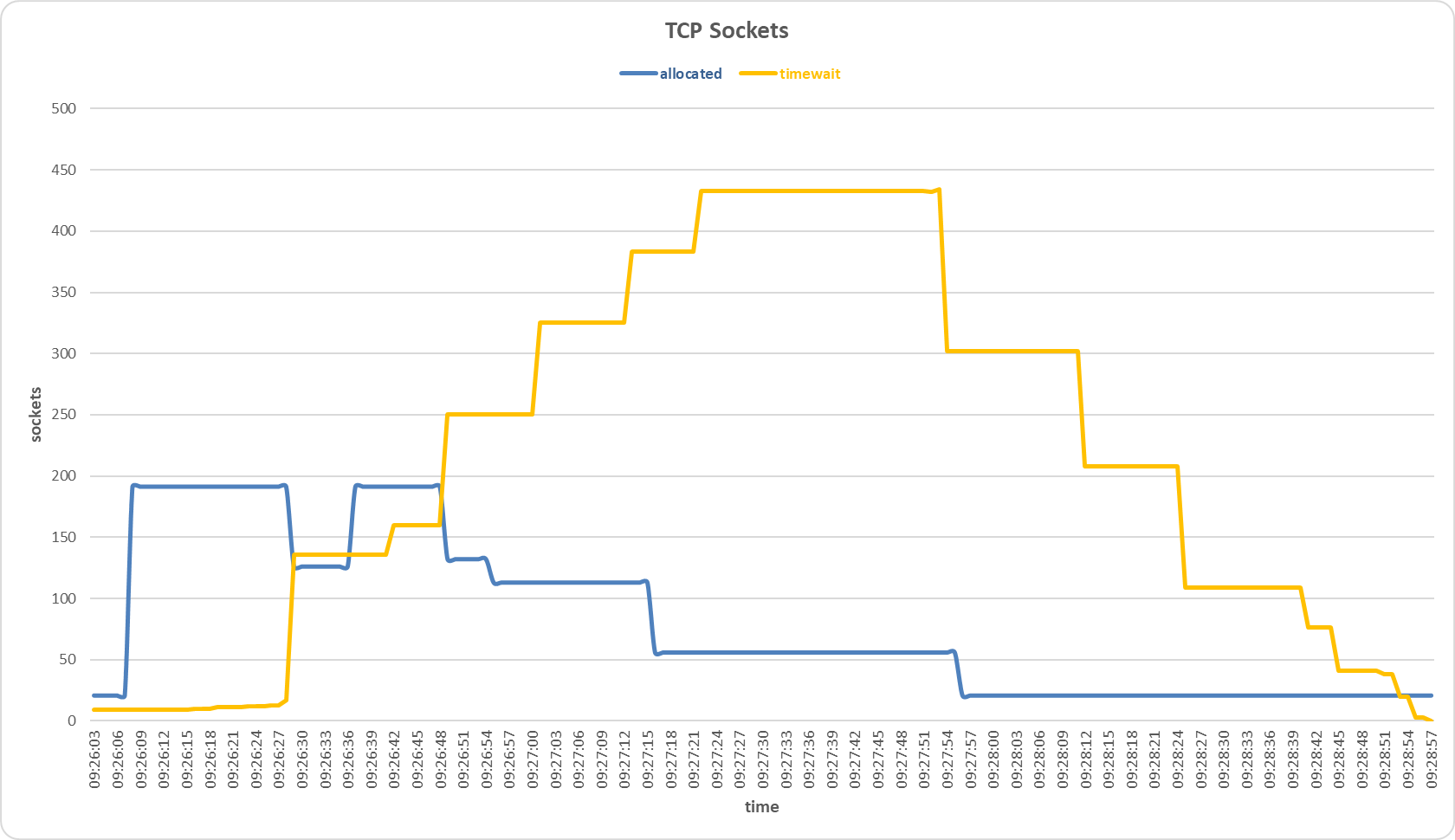
Sockets allocated and timewait on the secondary server during TCP SYN Flood attack with Multilayer Perceptron sensor.
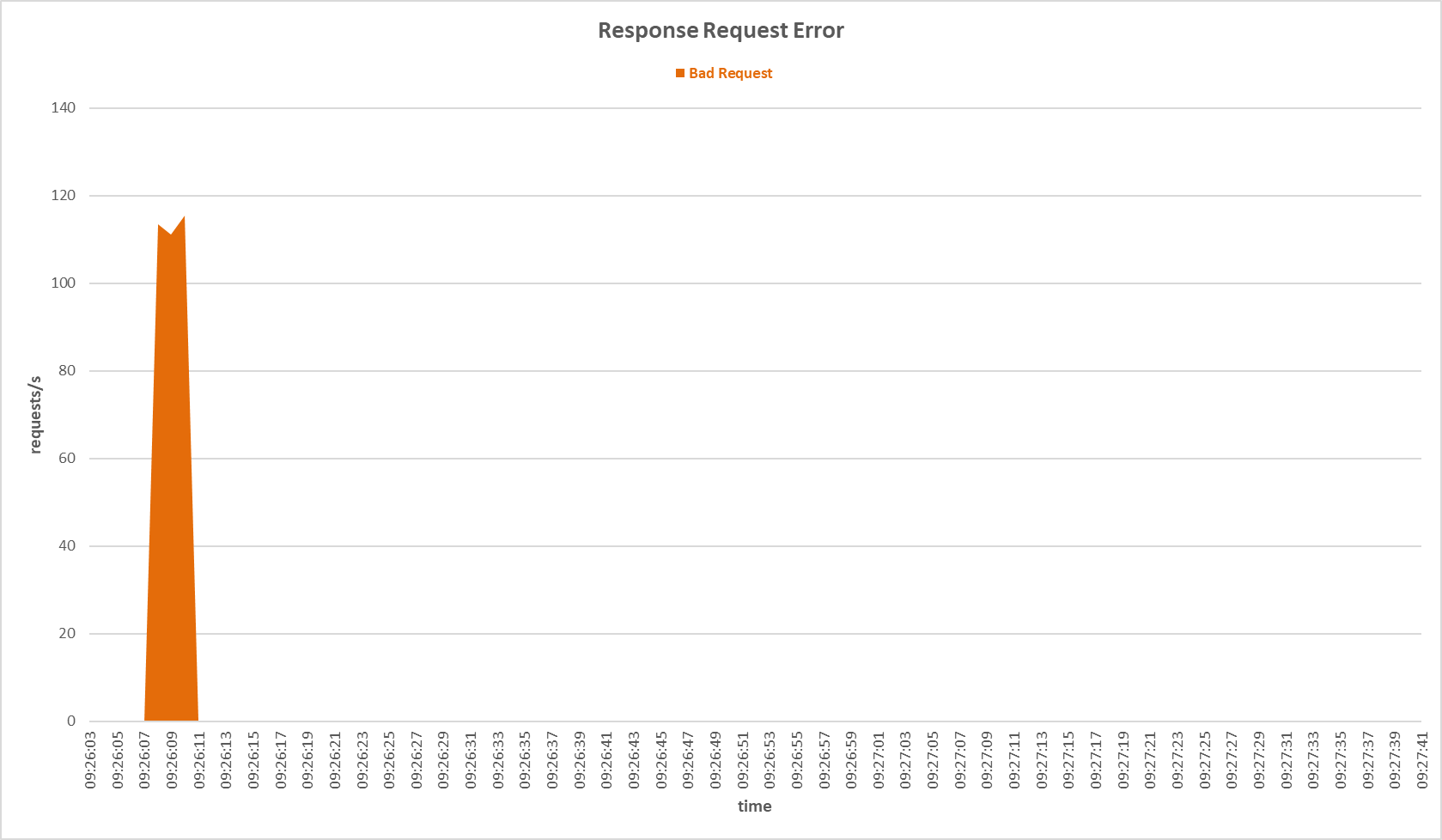
Request errors occurred on the primary server during TCP SYN Flood attack with Multilayer Perceptron sensor.
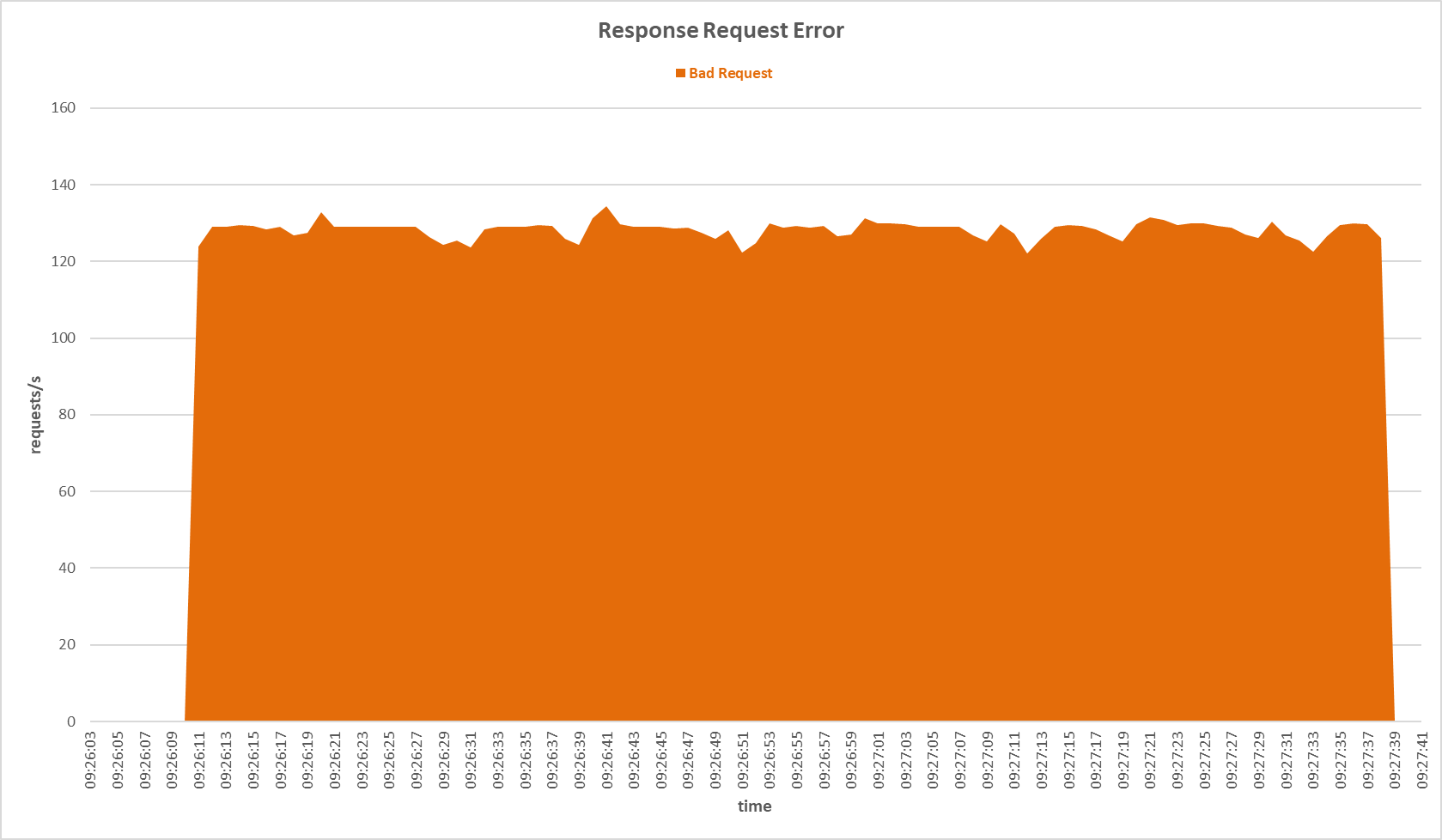
Request errors occurred on the secondary server during TCP SYN Flood attack with Multilayer Perceptron sensor.
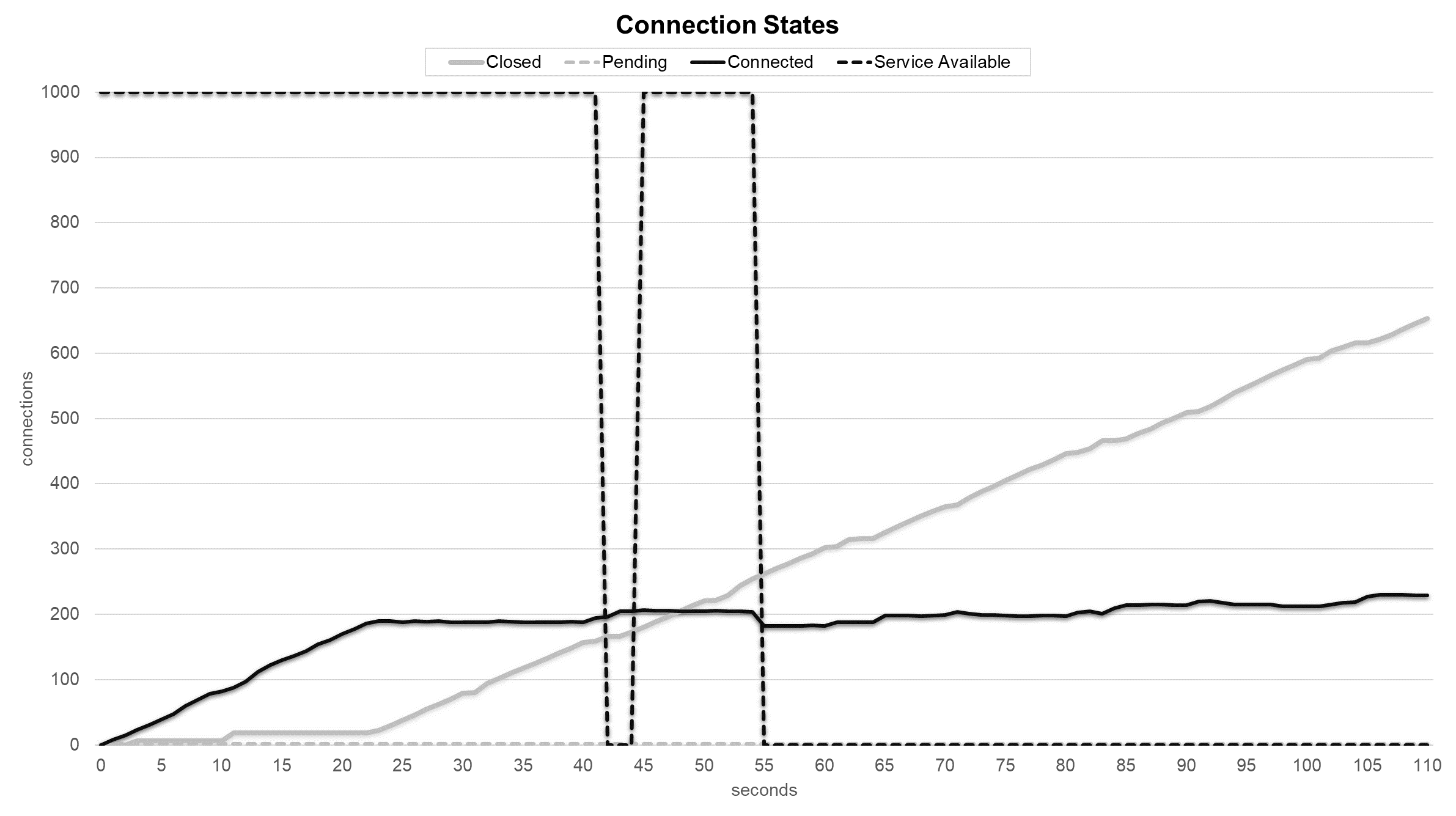
Service and connection states during TCP SYN Flood attack with Multilayer Perceptron sensor.
Project demo
Here the functioning of the proposed project is demonstrated. For the demo, the "Blue" server is the primary server, and the "red" server is the secondary server. The operation of the Machine Learning sensor and the SDN Controller are demonstrated.